Clop ransomware is currently one of the oldest [ almost from last 4 years] and most active group as demonstrated from Moveit execute saga from May 2023. They have currently 246 victims listed on the data leak site and from Moveit vulnerability as of now on 5th August 2023, 591 organizations are impacted. First part is focusing on threat actor profiling and possible cause of Clop ransomware hackers evoluation.
Threat Actor Profiling to Discover Clop Ransomware Authors:
In this section, we will research about possible threat actors behind the curtain and operating clop ransomware. Threat actor profiling is the process of gathering and analyzing information about a specific threat actor or group in order to understand their goals, capabilities, and methods. This information can then be used to develop mitigation strategies and to protect against future attacks.
There are a number of factors that can be used to profile a threat actor, including:
- Goals: What are the threat actor’s goals? Are they financially motivated, politically motivated, or something else?
- Capabilities: What tools and techniques does the threat actor have at their disposal? Are they sophisticated or relatively unskilled?
- Methods: How does the threat actor typically operate? Do they use social engineering, phishing, or other methods to gain access to systems?
- Motivation: What is the threat actor’s motivation? Are they trying to steal data, disrupt operations, or something else?
- Attribution: Can the threat actor be attributed to a specific group or organization?
Threat actor profiling can be a complex and challenging task, but it is essential for organizations that want to protect themselves from cyberattacks. By understanding the threat actors that they are facing, organizations can develop more effective mitigation strategies and reduce their risk of being attacked.
Brains behind evolution of Clop Ransomware – Historical Analysis
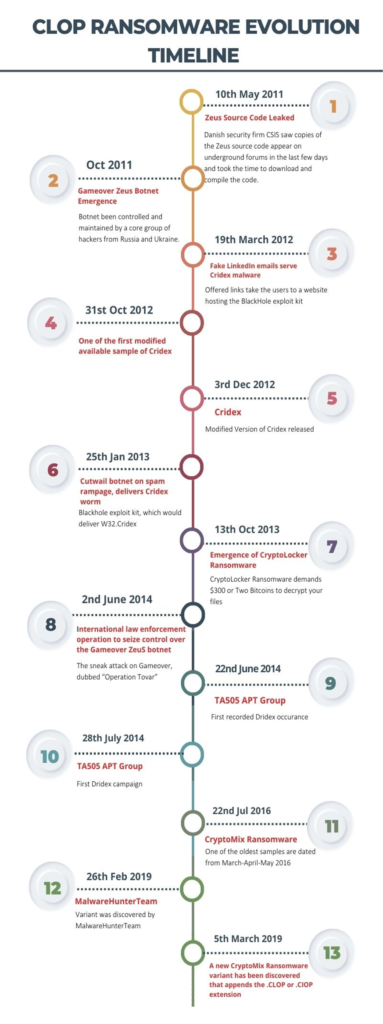
1. As from inline timeline, the historical evaluation of ransomware can be linked with Zeus Botnet times. In 2011, one of the most active execute kits like BlackHole was used in creation of Zeus Botnet.
2. Zeus has been sold in the criminal underground for roughly $5,000. However, the release of the Zeus source code will not only eliminate the market for Zeus licenses, but will also make the kit available to a new class of attacker
3. Along 2011, One of the most popular uses of Gameover has been as a platform for seeding infected systems with CryptoLocker
4. Also, during 2011, Microsoft intelligence spotted first Cridex malware payload which can act as a worm. This worm was capable of steal personal information, including online banking user names and passwords. It can also steal user names and passwords for social networking websites. https://www.microsoft.com/en-us/wdsi/threats/malware-encyclopedia-description?name=win32%2Fcridex
5. In Oct 2013, Emergence of CryptoLocker Ransomware discovered. https://thehackernews.com/2013/10/cryptolocker-ransomware-demands-300-to.html
6. Nearly as soon as Zeus was taken down, the “zero” version of Cridex stopped working. Dridex version 1.100 appeared almost exactly one month afterward. Dridex is the successor to a similar piece of malware called Cridex which also targets bank account. Its delivered in the form of a macro, buried in a Microsoft Word document in a spam email message.
7. On 2nd June 2014, International law enforcement operation to seize control over the Gameover ZeuS botnet which was Collaborative effort by investigators like FBI, Europol, and the UK’s National Crime Agency and Security firms like CrowdStrike, Dell SecureWorks, Symantec, Trend Micro and McAfee.
8. On 28th July 2014, TA505 APT Group emerged with first widespread Dridex campaign.
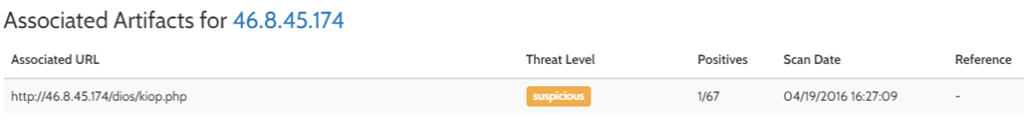
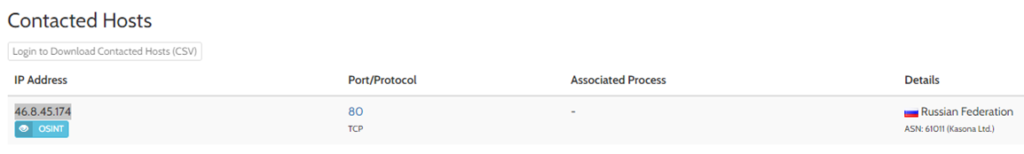
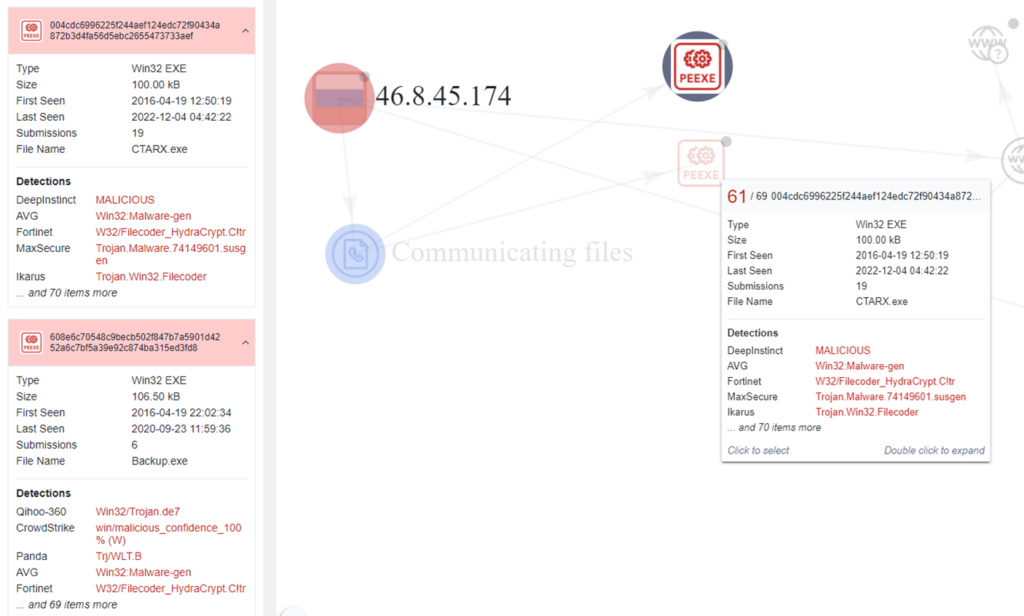
9. On 19th April 2016, first sample of CryptoMix ransomware spotted in which Data about encrypted files is sent to a C&C server located on IP addresses assigned to Russia at IP 46.8.45.174. [address: Bazarova, Kamyshin, 403876, Russia]
10. On 26th Feb 2019, A new CryptoMix Ransomware variant has been discovered that appends the .CLOP or .CIOP extension to encrypted files.
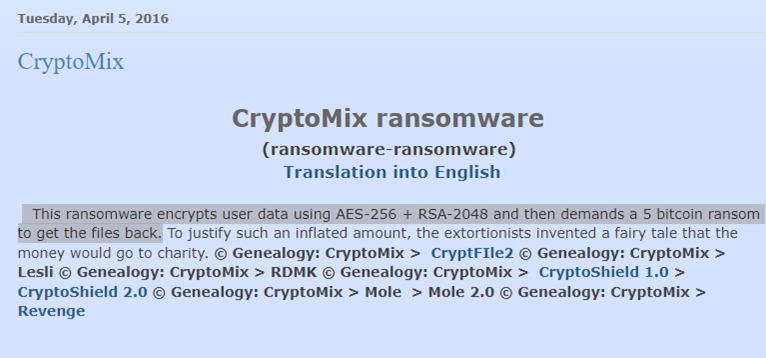
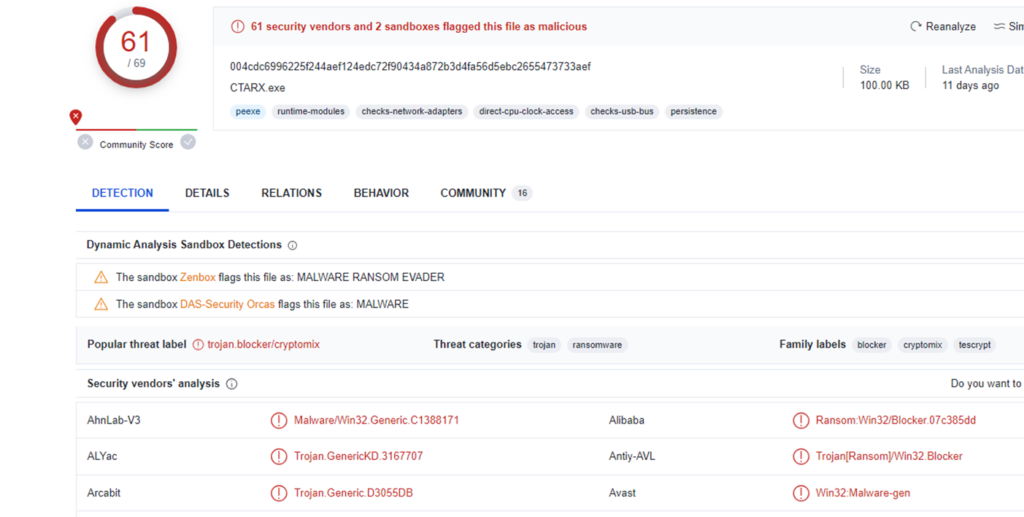
CryptoMix ransomware – In 2016, one of the ransomware strain appear in the wild capable of encrypting files known as CryptoMix Ransomware. From oldest threat actor profiling, we could see that Clop ransomware is a variant of Cryptomix Ransomware which was active in April 2016. The first ransomware victim was marked on 24th April 2016. The ransomware was at basic level. This ransomware encrypts user data using AES-256 + RSA-2048 and then demands a 5-bitcoin ransom to get the files back.
1. The name Cryptomix is a combination of two separate ransomware families CryptXXX and CryptoWall and has been given this name due to similarities between the families. First ransomware sample compiled date is – Creation Time – 2016-04-19 06:15:06 UTC
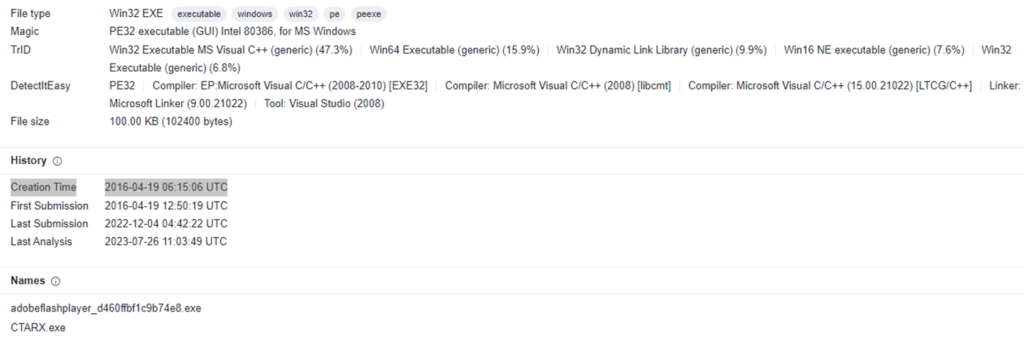
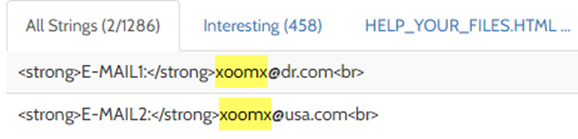
2. As from first ransomware notes available, email addresses used as E-MAIL1: xoomx@dr.com | E-MAIL2: xoomx@usa.com
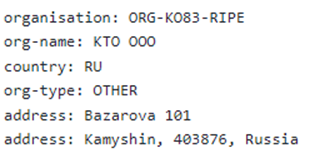
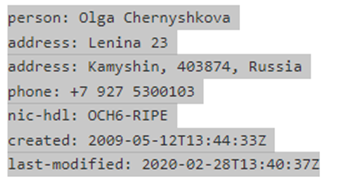
3. Data about encrypted files is sent to a C&C server located on IP addresses assigned to Russia at IP 46.8.45.174. [address: Bazarova, Kamyshin, 403876, Russia] by a Registered Personal named Olga Chernyshkova
4. Ransomware renders systems inoperable by encrypting files that are normally used for ordinary operations.
5. Affected consumers who choose to pay the threat actors behind ransomware operations in exchange for data access may not receive their files back. There is also no guarantee that threat actors would keep their half of the bargain when the ransom is paid.
6. Affected individuals who choose to pay the threat actors may become future targets of ransomware campaigns.
7. Data held hostage that was not returned to users or destroyed after the ransom was paid might be utilized by threat actors to (a) sell on the black market or (b) develop a profile of the user to target in the future.
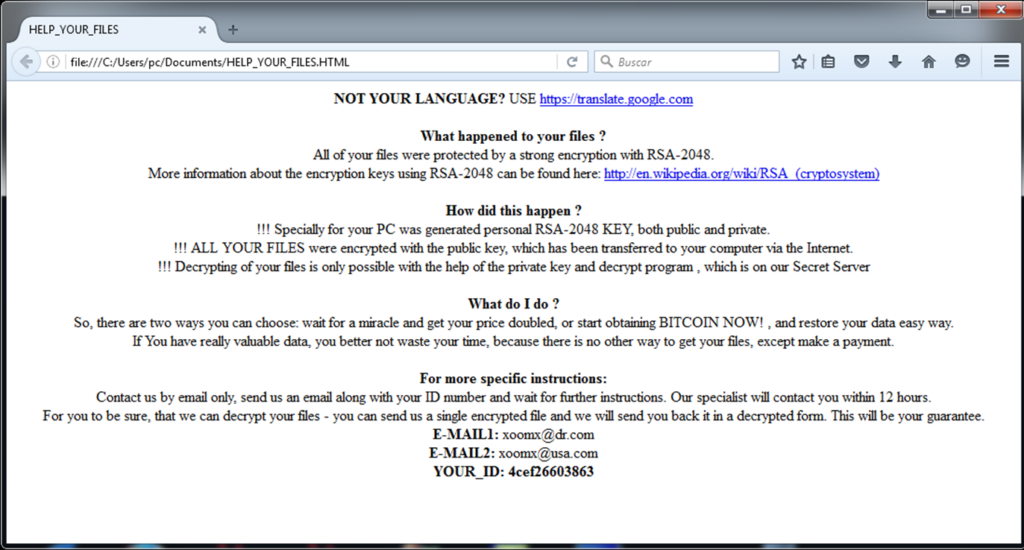
First Clop Ransomware variant compiled and spotted in the wild
Clop ransomware is currently one of the oldest [ almost from last 4 years] and most active group as demonstrated from Moveit execute saga from May 2023. They have currently 246 victims listed on the data leak site. This article is focusing on threat actor profiling of various groups entities are operating with this ransomware ecosystems.
First known attacks of Clop Ransomware
- 26th Feb 2019 – MalwareHunterTeam on their twitter handle posted information about new variant of CryptoMix ransomware which is adding extensions as. Clop to the encrypted files.
- This ransom notes also contain the emails unlock@eqaltech.su, unlock@royalmail.su, and kensgilbomet@protonmail.com that can be used to contact the attackers for payment instructions.
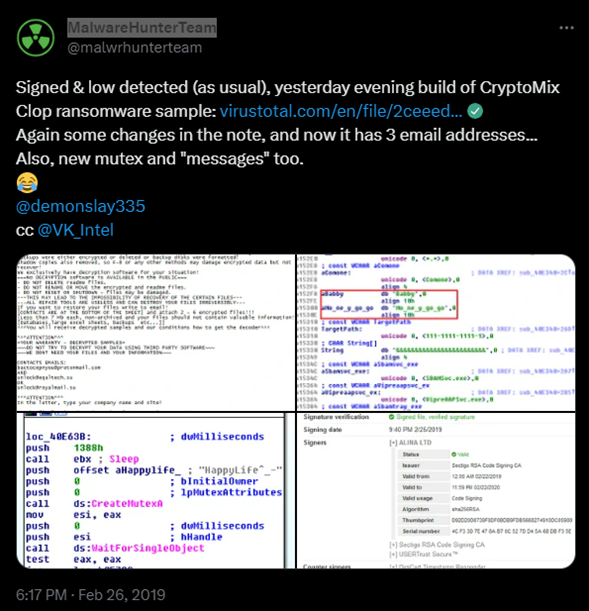
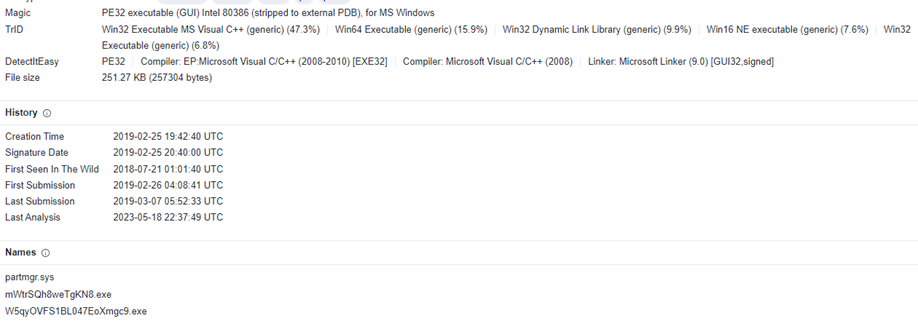
3. First ransomware payload sample partmgr.sys, executed from 25th Feb 2019 as validated from Creation Timestamp – 2019-02-25 19:42:40 UTC.
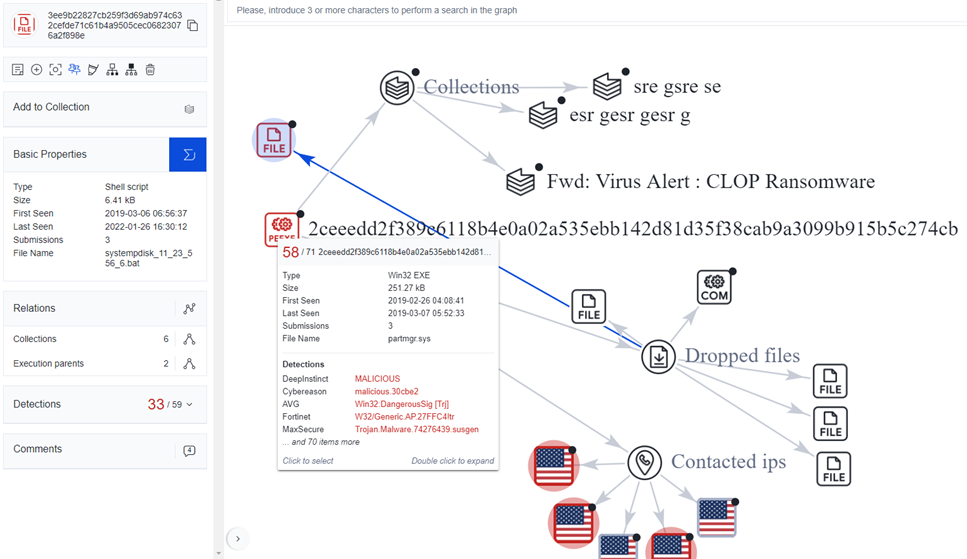
Second Sample Discovered: 5th March 2019
A new CryptoMix Ransomware variant has been discovered that appends the .CLOP or .CIOP extension which is covered by BleepingComputer
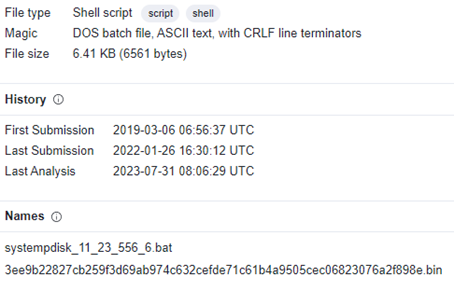
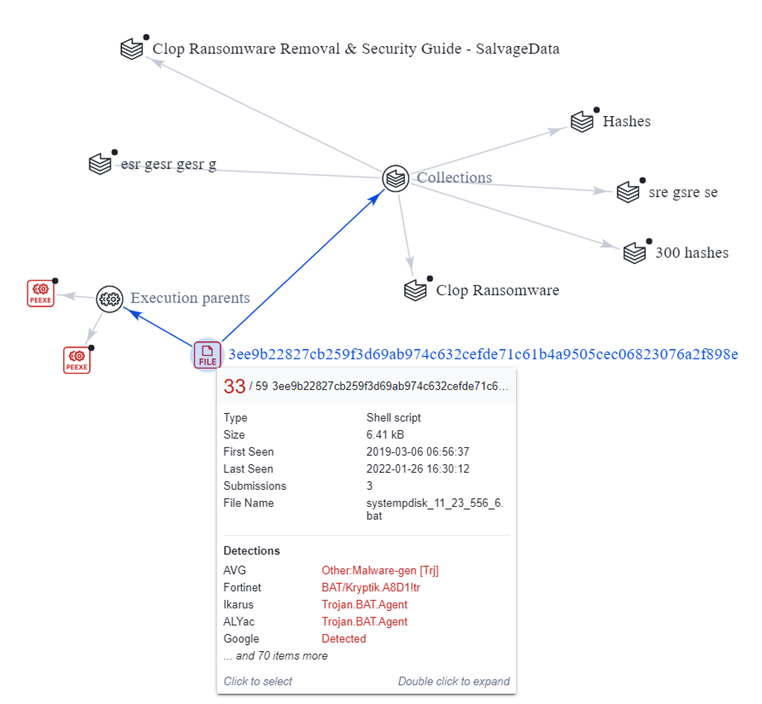
Execution from .bat file noticed named clearnetworkdns_11-22-33.bat which can disable multiple AV solutions as reported on 5th March 2019 article by bleepingcomputer. One more oldest sample we could spot and still available as systempdisk_11_23_556_6.bat which is First Submitted on 6th March 2019, 2019-03-06 06:56:37 UTC
First ransomware .bat file execution sample compiled date – Creation Time – 2019-03-06 06:56:37 UTC
Arrests made thus far in connection with known members of cybercrime
As of August 2023, there have been a total of six arrests made in connection with known members of the Clop ransomware cybercrime group. These arrests were made in June 2021, as part of a joint operation by law enforcement agencies in Ukraine, South Korea, and the United States.
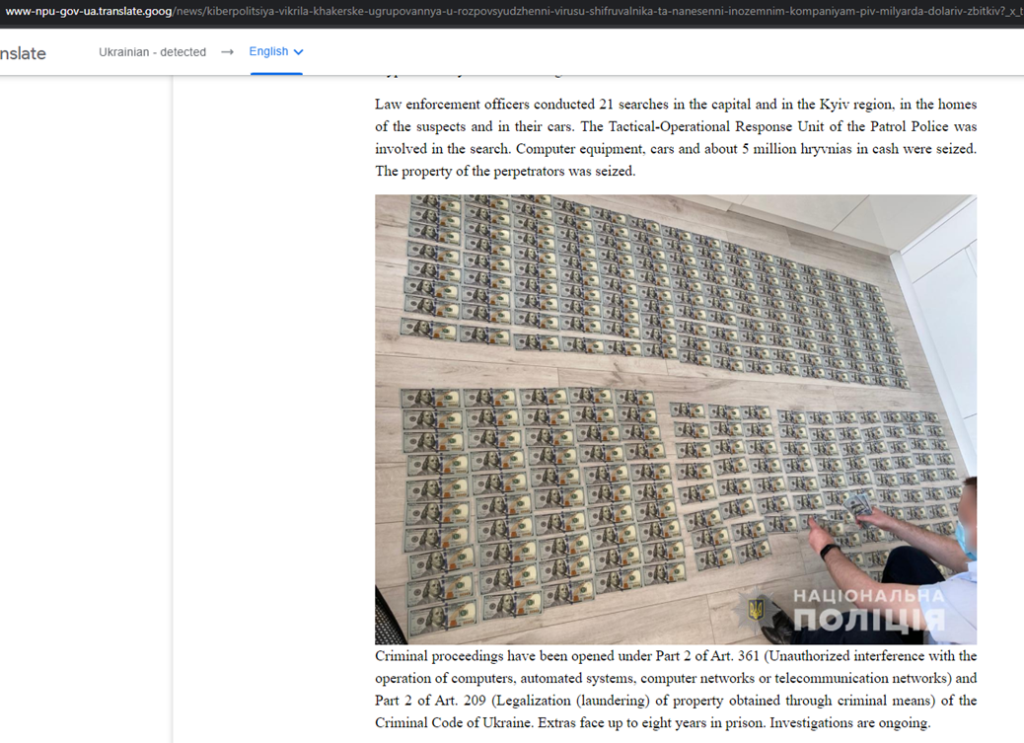
- Posted on June 16, 2021 at 11:30 am In Ukraine, accused gang members have been apprehended. In June 2021, Interpol, Europol, and law enforcement agencies from South Korea, Ukraine, and the United States collaborated on an operation. INTERPOL-led-operation-takes-down-prolific-cybercrime-ring – https://www.interpol.int/News-and-Events/News/2021/INTERPOL-led-operation-takes-down-prolific-cybercrime-ring . The global strike, codenamed Operation Cyclone, followed global police investigations into Cl0p ransomware.
- The resulting intelligence enabled Ukrainian police to search more than 20 houses, businesses and vehicles, confiscate property and computers, and seize USD 185,000 in cash assets, as well as to make the six arrests. https://www.youtube.com/watch?v=PqGaZgepNTE
- The six alleged members of the Clop ransomware gang are currently being held in custody in Ukraine. They are facing charges of cybercrime, extortion, and money laundering. The arrests in Ukraine are a significant blow to the Clop ransomware gang. They send a message to other ransomware groups that they will be brought to justice. The arrests were also made possible by the close cooperation between law enforcement agencies around the world.
Arrest of Tank in Geneva in Oct 2022
- 15th Nov 2022, Vyacheslav Igorevich Penchukov is the accused 40-year-old Ukrainian leader of a prolific cybercriminal group Zeus Botnet operated under the name of JabberZeus Crew. He was arrested in Geneva, Switzerland in November 2022. https://krebsonsecurity.com/2022/11/top-zeus-botnet-suspect-tank-arrested-in-geneva/
- The Zeus Botnet is a malware program that was first discovered in 2007. It is a banking trojan that steals financial information from victims’ computers. The JabberZeus Crew is a group of cybercriminals who used the Zeus Botnet to steal millions of dollars from victims around the world.
- Penchukov is accused of being the leader of the JabberZeus Crew. He is charged with conspiracy to commit wire fraud, computer intrusion, and money laundering. If convicted, he could face up to 20 years in prison.
- The arrest of Penchukov is a significant victory for law enforcement in the fight against cybercrime. The Zeus Botnet was one of the most prolific malware programs in the world, and the JabberZeus Crew was one of the most active groups using it. The arrest of Penchukov sends a message to other cybercriminals that they will be brought to justice.

This is a continuation story and will be shared in next blog as attacks are still getting disclosed as of 5th August 2023.