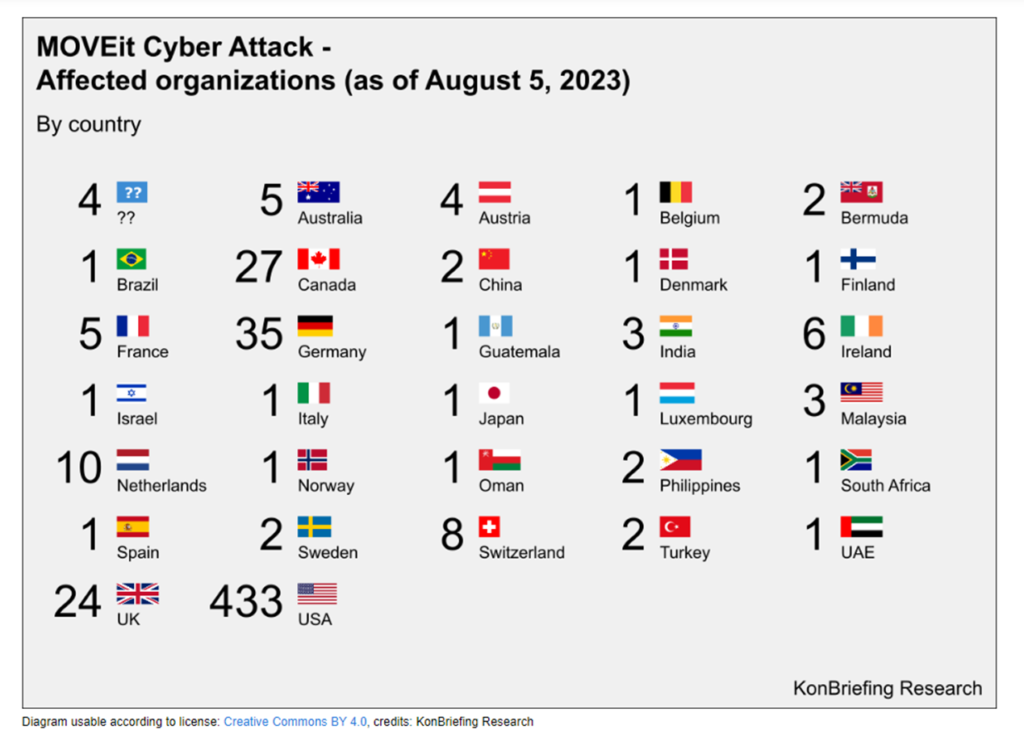
This is a second part of analysis, which is focusing on recent attacks of Clop ransomware group In 2023, clop executed 2 zero day vulnerabilities which caused impact of 500 plus organizations.
- The CLOP ransomware gang executed a vulnerability in the MOVEit Transfer software to gain unauthorized access to sensitive data. The vulnerability, which was tracked as CVE-2023-34362, allowed attackers to execute arbitrary SQL commands on MOVEit Transfer servers. This allowed them to steal data from the servers, including files, passwords, and other sensitive information.
- The Cybersecurity and Infrastructure Security Agency (CISA) and the FBI issued an alert on June 7, 2023, warning organizations about the Clop ransomware attack and the MOVEit Transfer vulnerability. They urged organizations to patch the vulnerability as soon as possible and to implement other security measures to protect their networks from ransomware attacks.
- From threat intel analysis, it was clear that early executed Development dated back to July 2021 in which CLOP actors were testing MoveIt vulnerability.
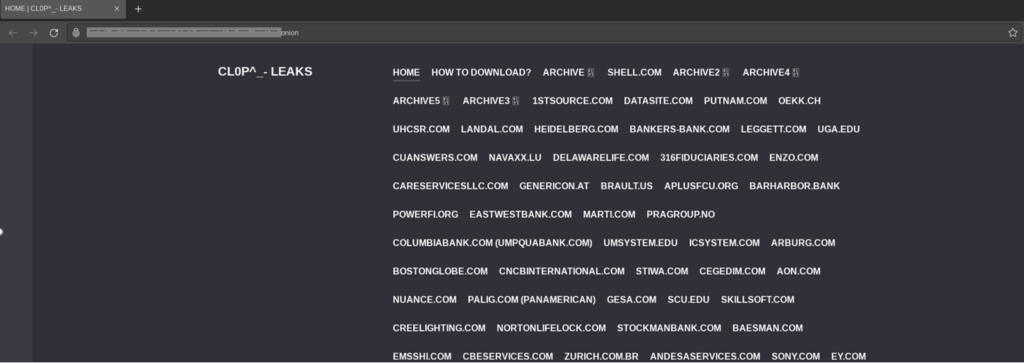
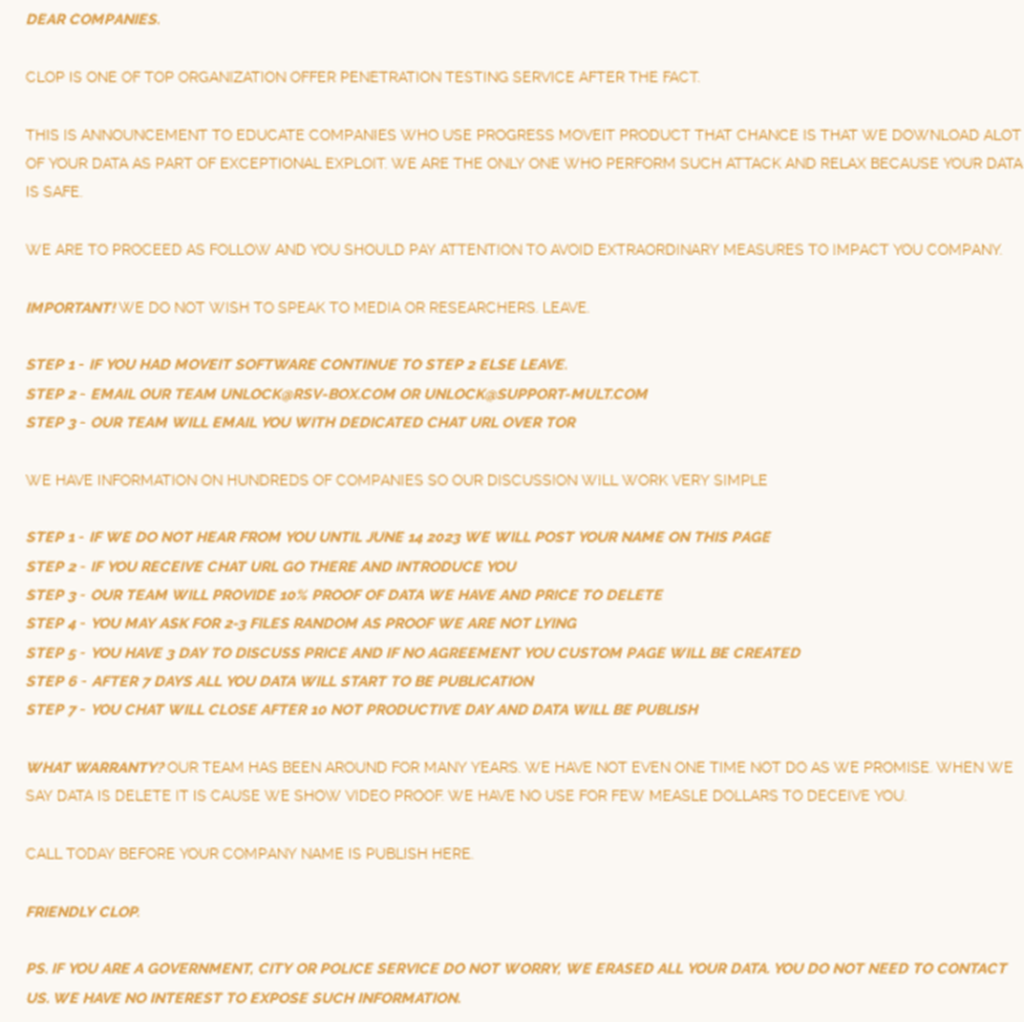
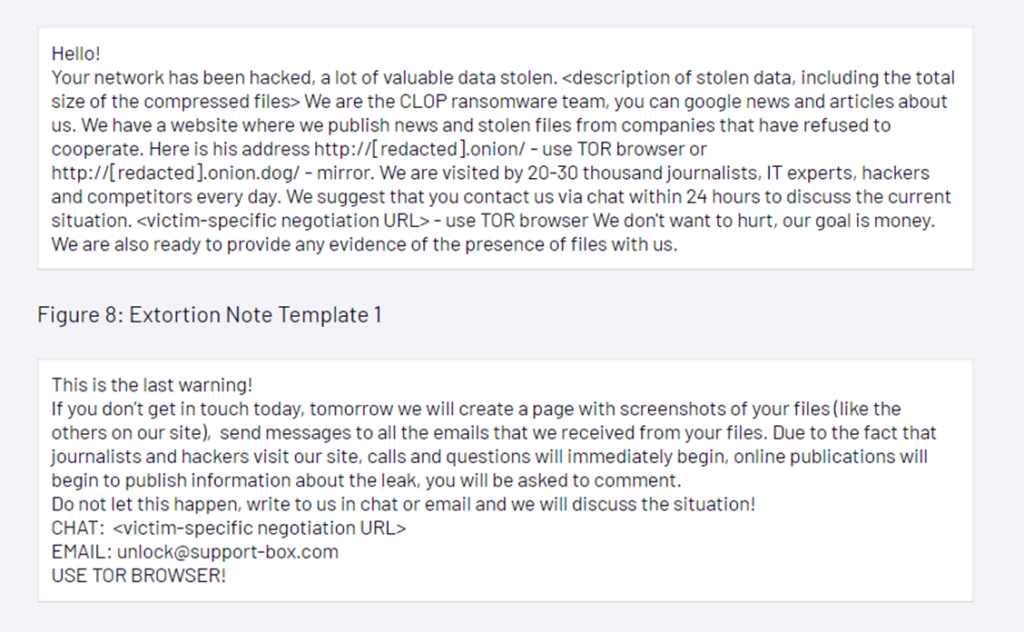
- Clop made a claim on its data-leak site, “>_CLOP_-LEAKS” – the dark web portal where it distributes data belonging to Clop victims who choose not to pay the demanded ransom – on June 6, 2023. Clop claimed in this post to have stolen data from hundreds of companies using the MOVEit bug and guided victims on how to initiate extortion discussions with Clop, setting a June 14, 2023 deadline. Clop pledged in this article that any impacted organization that does not contact Clop before this date will have its data revealed on Clop’s data-leak site. Clop indicated that after 10 days of fruitless negotiations, data for victims will be published.
APT Groups using CLOP Ransomware-
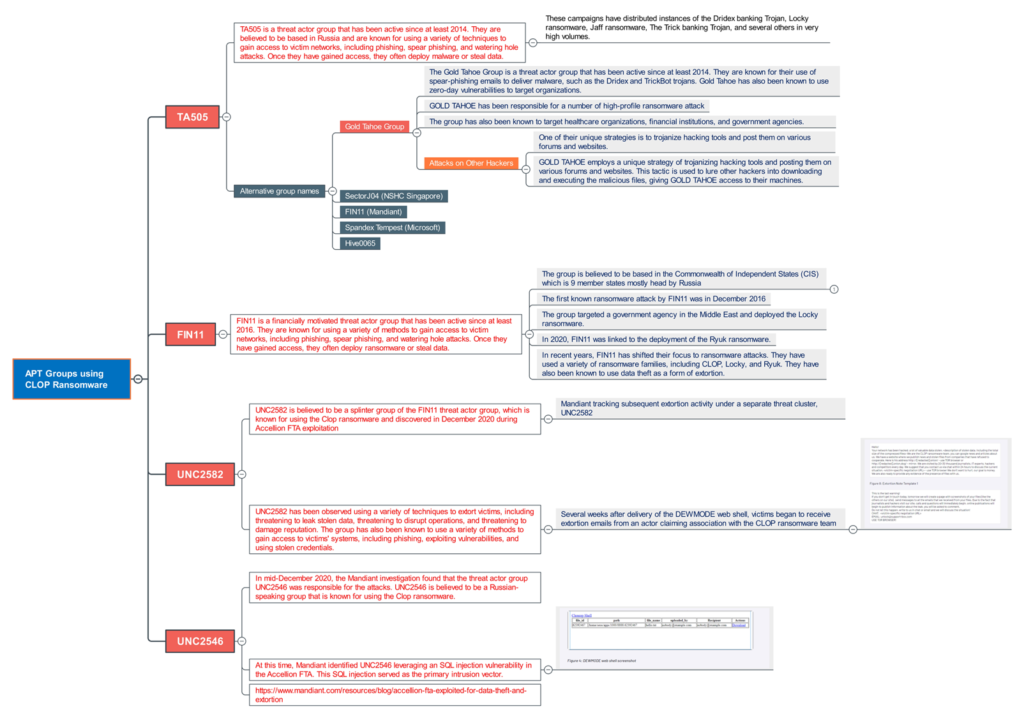
- TA505 – TA505 is a threat actor group that has been active since at least 2014. They are believed to be based in Russia and are known for using a variety of techniques to gain access to victim networks, including phishing, spear phishing, and watering hole attacks. Once they have gained access, they often deploy malware or steal data. These campaigns have distributed instances of the Dridex banking Trojan, Locky ransomware, Jaff ransomware, The Trick banking Trojan, and several others in very high volumes.
a. One of the Alias is termed as Gold Tahoe Group – The Gold Tahoe Group is a threat actor group that has been active since at least 2014. They are known for their use of spear-phishing emails to deliver malware, such as the Dridex and TrickBot trojans. Gold Tahoe has also been known to use zero-day vulnerabilities to target organizations.
b. GOLD TAHOE employs a unique strategy of trojanizing hacking tools and posting them on various forums and websites. This tactic is used to lure other hackers into downloading and executing the malicious files, giving GOLD TAHOE access to their machines.
c. First Observed Date: 22nd June 2014
d. The group is thought to be centered in the Commonwealth of Independent States (CIS), a 9-member regional intergovernmental organization in Eurasia led by Russia.
1.Armenia
2.Azerbaijan
3.Belarus
4.Kazakhstan
5.Kyrgyzstan
6.Moldova (suspended participation)
7.Russia
8.Tajikistan
9.Uzbekistan
- FIN11 – It was reported in 2020 that FIN11 — a financially driven hacking outfit — used Clop ransomware and threatened their victims with the publication of exfiltrated data. FIN11 used zero-day vulnerabilities in Kiteworks’ (previously Accellion’s) legacy file transfer appliance (FTA) to infiltrate the victims’ networks.
- UNC2546- The Mandiant investigation concluded in mid-December 2020 that the attacks were carried out by the threat actor group UNC2546. UNC2546 is thought to be a Russian-speaking organization that uses the Clop ransomware. Mandiant discovered UNC2546 executing a SQL injection vulnerability in the Accellion FTA during this time. Multiple incidents were uncovered in which a web shell dubbed DEWMODE was used to exfiltrate data from Accellion FTA devices, with SQL injection serving as the major intrusion vector.
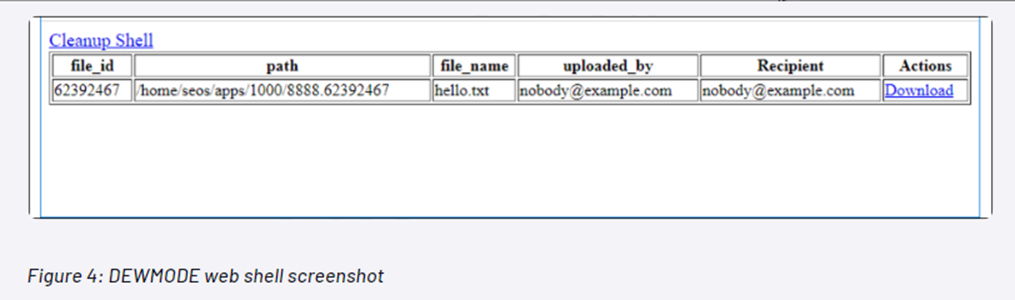
- UNC2582 – UNC2582 is believed to be a splinter group of the FIN11 threat actor group, which is known for using the Clop ransomware and discovered in December 2020 during Accellion FTA execution. As Mandiant tracking subsequent extortion activity under a separate threat cluster, UNC2582 in which UNC2582 has been observed using a variety of techniques to extort victims, including threatening to leak stolen data, threatening to disrupt operations, and threatening to damage reputation. The group has also been known to use a variety of methods to gain access to victims’ systems, including phishing, executing vulnerabilities, and using stolen credentials. https://www.mandiant.com/resources/blog/accellion-fta-exploited-for-data-theft-and-extortion . Several weeks after delivery of the DEWMODE web shell, victims began to receive extortion emails from an actor claiming association with the CLOP ransomware team.
Zero-Days executed till Date
The Clop ransomware gang has been known to execute zero-days in a number of different software applications, including:
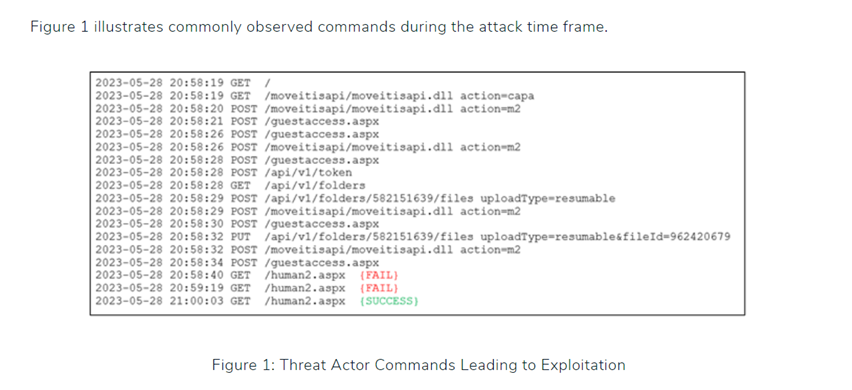
- MOVEit Transfer: A managed file transfer (MFT) solution from Progress Software. The Clop gang executed a zero-day vulnerability in MOVEit Transfer on May 27, 2023. https://www.kroll.com/en/insights/publications/cyber/clop-ransomware-moveit-transfer-vulnerability-cve-2023-34362.
CVE-2023-34362 allows for SQL injection, which can result in unauthorized access to sensitive data, such as passwords, credit card details, or personal user information.
2. GoAnywhere MFT: A secure file transfer (SFT) solution from Fortra. The Clop gang executed a zero-day vulnerability in GoAnywhere MFT on February 14, 2023.
- CVE-2023-0669 Fortra (previously HelpSystems) GoAnywhere MFT is vulnerable to pre-authentication command injection in the License Response Servlet as a result of deserializing an arbitrary attacker-controlled object. This bug was fixed in version 7.1.2. The attack vector of this executed requires access to the application’s administrative console, which is typically only accessible from within a private company network, via VPN, or by allow-listed IP addresses (when running in cloud environments such as Azure or AWS).
3. Accellion FTA: A managed file transfer (MFT) solution from Accellion. The Clop gang executed a 4 zero-day vulnerability in Accellion FTA on December 8, 2020. https://threatpost.com/accellion-zero-day-attacks-clop-ransomware-fin11/164150/
Four zero-day security holes were executed in the attacks, according to the investigation:
i. CVE-2021-27101 – SQL injection via a crafted Host header
ii. CVE-2021-27102 – OS command execution via a local web service call
iii. CVE-2021-27103 – SSRF via a crafted POST request
iv. CVE-2021-27104 – OS command execution via a crafted POST request
4. SolarWinds Serv-U Managed File Transfer: A managed file transfer (MFT) solution from SolarWinds. The Clop gang executed a zero-day vulnerability in SolarWinds Serv-U Managed File Transfer in December 2020.
Prominent attacks executed by Clop ransomware group:
Clop Ransomware leveraged two zero-day vulnerabilities in 2023, the first in March 2023 CVE-2023-0669 called zero-day vulnerability in GoAnywhere MFT and the second in May 2023 identified as CVE-2023-34362 to carry out the MoveIT Supply Chain Attack in June and July 2023.
1. Targeted Country – Canada:
By executing a remote code execution flaw in Fortra’s GoAnywhere secure file transfer tool enables attackers to gain remote code execution on unpatched GoAnywhere MFT instances with their administrative console exposed to Internet access.
a. Zero-day vulnerability in GoAnywhere MFT
i.March 23, 2023 - City of Toronto confirms data theft, Clop claims responsibility. h[x][x] ps://www.bleepingcomputer.com/news/security/city-of-toronto-confirms-data-theft-clop-claims-responsibility/
b. MoveIT Supply Chain Attack in June and July 2023
i. 11th July 2023 - Air Canada
ii. 11th July 2023 - Laurentian Bank of Canada
iii. 11th July 2023 - Staples Canada
iv. 11th July 2023 - Sun Life Assurance of Canada
v. 11th July 2023 - United Parcel Service Canada Ltd2. Targeted Country – United States Of America
i. 6th June 2023 – The Government of Nova Scotia – https://novascotia.ca/news/release/? id=20230606004 – The Government of Nova Scotia is the provincial government of the Canadian province of Nova Scotia. The capital of the province, Halifax, is Nova Scotia’s largest city and its political capital. The current Premier of Nova Scotia is Tim Houston, who was sworn into office in August 2021.
ii. 6th June 2023 – The American Board of Internal Medicine – https://blog.abim.org/moveit-transfer-vulnerability-affects-abim/
iii. 7th June 2023 – BORN Ontario – https://www.bornontario.ca/en/news/cybersecurity-incident-moveit.aspx
iv. 9th June 2023 – The US state of Illinois – https://ltgov.illinois.gov/news/press-release.26572.html
v. 15th June 2023 – The US state of Missouri
vi. 15th June 2023 – Louisiana’s Office of Motor Vehicles (OMV) – https://www.expresslane.org/alerts/ – As per press release statement from OMV believes that all Louisianans with a state-issued driver’s license, ID, or car registration have likely had the following data exposed to the cyber attackers: Name, Address, Social Security Number, Birthdate, Height, Eye Color, Driver’s License Number, Vehicle Registration Information, Handicap Placard Information
3. Targeted Country – United Kingdom
i. June 8, 2023 – British Airways – According to the Daily Telegraph https://www.telegraph.co.uk/business/2023/06/05/british-airways-and- boots-warn-staff-data-stolen-in-hack/ , BA compromised information included names, addresses, national insurance numbers and banking details and hack had affected staff paid through BA payroll in the UK and Ireland
ii.13th June 2023 Ofcom – Britain’s communications regulator Ofcom – Impact – Personal data of 412 Ofcom employees, was downloaded during the attack https://vulnera.com/newswire/uk-regulator-ofcom-hit-by-clop-ransomware-via-moveit-file-transfer-zero-day/
4. Other notable businesses impacted by Clop ransomware are as follows:
- June 8, 2023 – Boots – As per confirmation, some of our team members’ personal details” had been affected. Data involved in the attack included names, surnames, employee numbers, dates of birth, email addresses, the first lines of home addresses, and national insurance numbers. https://www.theguardian.com/technology/2023/jun/05/ba-boots-and-bbc-staff-details-targeted-in-russian-linked-cyber-attack
- July 14, 2023 – Shutterfly – Shutterfly, an online retail and photography manufacturing platform, is among the latest victims hit by Clop ransomware. Shutterfly offers photography-related services to consumers, the enterprise, and education through various brands, including Shutterfly.com, BorrowLenses, GrooveBook, Snapfish, and Lifetouch.
- June 27, 2023 – Siemens – Manufactures a wide range of industrial products, including industrial control systems (ICS), state-of-the-art power, heat generation units, renewable energy systems, on and off-site energy delivery systems, and flexible power transmission solutions. https://www.reuters.com/technology/siemens-energy-no-critical-data-was-compromised-after-moveit-data-breach-2023-06-27/
- June 27, 2023 – Schneider Electric – Schneider said in a statement that it was “currently investigating this claim.”July 7, 2023 – A MOVEIT hack resulted in the exposure of SHELL employee data – The company confirmed it had been caught up in the already infamous third-party hack of the file transfer application MOVEit in a statement on Wednesday (5 July). https://www.cybersecurityconnect.com.au/commercial/9279-shell-employee-data-breached-as-part-of-moveit-hack
- July 12, 2023 – Deutsche Bank confirms a customer data breach – Deutsche Bank AG has confirmed that a data breach on one of its service providers has exposed its customers’ data in a likely MOVEit Transfer data-theft attack. https://cybersafe.news/deutsche-bank-confirms-a-customer-data-breach/
These are few notable victims from current attacks and detailed count can be viewed from https://konbriefing.com/en-topics/cyber-attacks-moveit-victim-list.html