What is Offensive OSINT ?
- Offensive OSINT is the process of using information that is readily available to the public to assist in offensive security activities such as vulnerability research, social engineering evaluations, penetration testing, and red teaming exercises.
- While performing an attack, it is used to obtain information about a target company or person in order to find weaknesses that could be exploited.
- Similar tools and methods used in ethical hacking and cyber threat intelligence are also used in offensive OSINT, but the main goal is to collect data that may be used to assist planned offensive security assessments.
Offensive OSINT Tools and Techniques
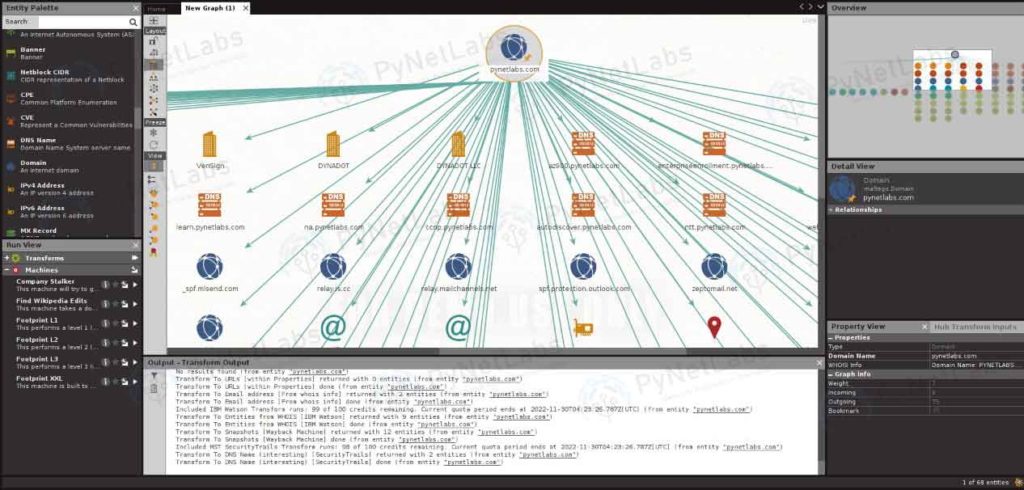
Maltego: Maltego is an effective open-source intelligence (OSINT) program that may be used to obtain data from a range of sources, such as websites, public records, and social media. It can also be used to locate people and find vulnerabilities.
Google Dorks: Google Dorks are specialized search operators that are useful for locating particular kinds of online content. For instance, to locate websites that have been compromised or are open to attack, employ a Google Dork.
visit: https://www.techtarget.com/whatis/definition/Google-dork-query
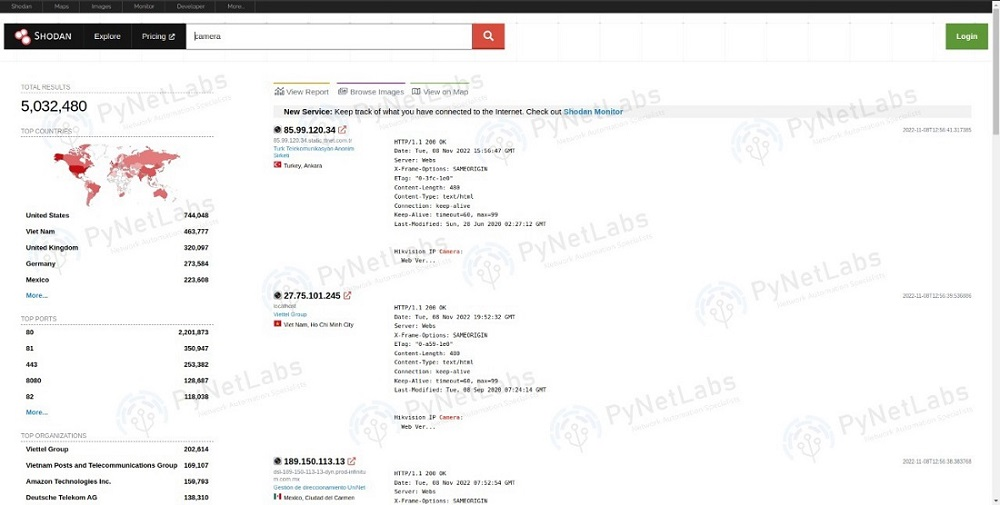
Shodan: Shodan is a search engine that looks for vulnerabilities and open ports on the internet. Vulnerable equipment, including routers, web servers, and Internet of Things devices, can be identified using it.
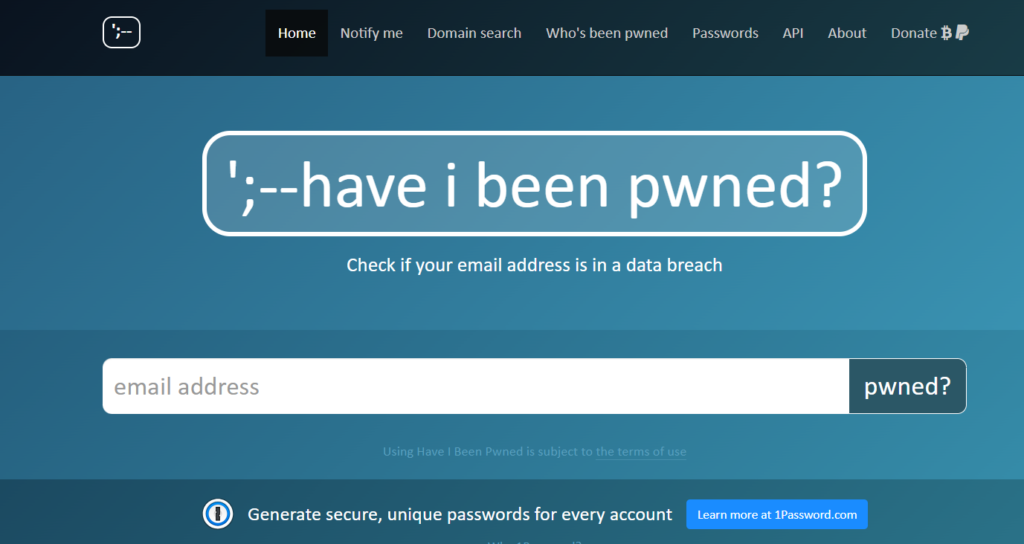
HaveIBeenPwned: This website lets you determine whether a data breach has compromised your password or email address. It’s a useful tool for figuring out possible security threats.
Spyse: Spyse is a paid OSINT tool with many functions, such as risk assessment, social media surveillance, and data enrichment. For companies that require a more complete OSINT solution, it is a good choice.
Recon-ng: To automate the gathering of OSINT data, utilize the free and open-source Recon-ng framework. For companies in need of an expandable and customizable OSINT solution, it is an excellent choice.
ZoomEye: ZoomEye is a for-profit search engine that maps vulnerabilities, open ports, and other security threats on the internet. For businesses that want a thorough and current understanding of their network security posture, it is a suitable choice.
Using offensive OSINT techniques, one can obtain a variety of data on an organization, such as:
1. Contact Information: This can be used to find contractors, workers, and other people who might have access to private data.
2. IP addresses: These can be used to map the network architecture of an organization and pinpoint any possible weak points.
3. Social media profiles: These can be used to learn details about the personal lives of employees, which can then be used in social engineering schemes.
4. Publicly available documents: These can include personnel handbooks, financial reports, and other documents that might include sensitive data.
Current Events and News
- Information security teams conducting penetration tests and red team exercises are using more offensive OSINT techniques.
- emergence of certifications and training programs specifically focused on offensive OSINT for security professionals.
- Due to possible privacy violations or unforeseen effects, offensive OSINT raises legal and ethical considerations; guidelines are currently being developed.
- Offensive OSINT teams have access to abundant data sources for planning evaluations thanks to high-profile data breaches made possible by negligent security procedures.
- Wojciech was an offensive OSINT specialist who gathered information to bring down criminal organizations and fraudulent classifieds websites.
- Organizations like the Offensive Security organization which provide offensive OSINT training and certification.
- Political goals are advanced by hacktivist groups and anonymous hackers through the use of offensive OSINT.
It is important to remember that offensive OSINT should only be used for legal activities like penetration testing, security research, and law enforcement inquiries. It is illegal to use offensive OSINT for criminal activities like identity theft or cybercrime.