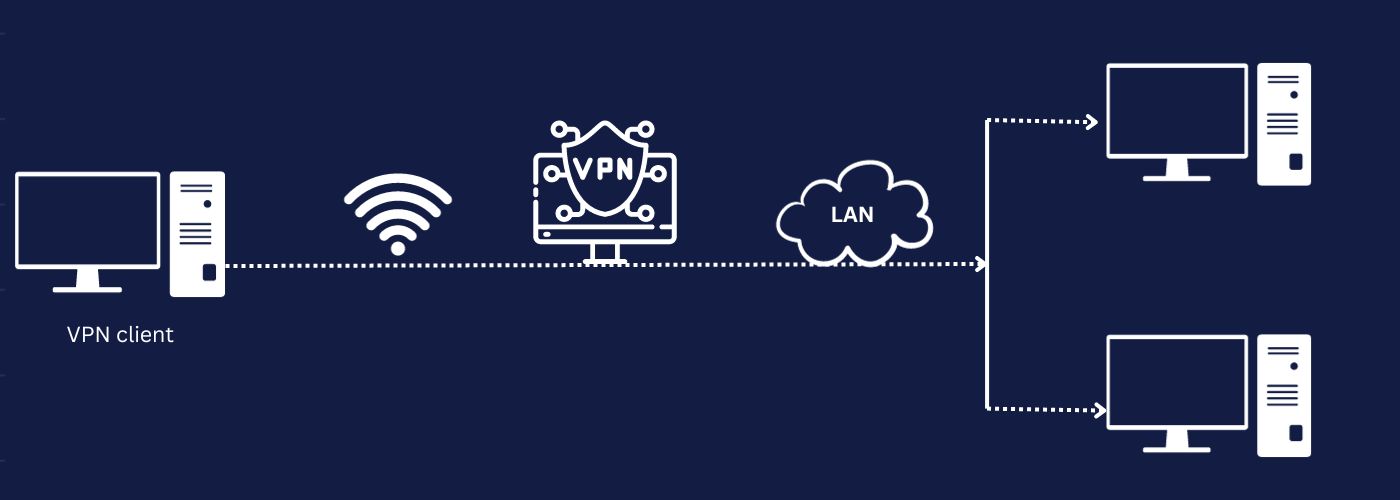
What is Tunneling Protocol?
A tunneling protocol is a network protocol that encapsulates one protocol’s data within the payload of another. This method lets data to be transmitted between devices or networks that do not natively support the encapsulated protocol.
Tunneling protocols provide a virtual network tunnel, or tunnel, through which encapsulated data can be sent. The tunneling protocol augments the original protocol’s data with additional headers and/or trailers, thereby enclosing it within the new protocol. When the data arrives at its destination, the tunneling protocol eliminates the superfluous headers and trailers, allowing the encapsulated data to be extracted.
Tunneling protocols are commonly used for various purposes, including:
- Virtual Private Networks (VPNs): Tunneling protocols such as IPsec, OpenVPN, and L2TP are used to construct secure and private connections over public networks such as the internet.
- IPv6 Transition: Tunneling protocols such as 6to4, Teredo, and ISATAP are used to carry IPv6 traffic through IPv4 networks, allowing the transition from the older IPv4 protocol to the newer IPv6 protocol to be more seamless.
- Remote Access: Tunneling technologies such as Secure Shell (SSH) enable secure access to remote systems via an untrusted network. SSH can construct secure tunnels for a variety of protocols, including file transfer (SFTP) and network service forwarding.
- Protocol Bypass: Tunneling can be used to circumvent firewalls and other network constraints by encapsulating restricted protocols within authorized protocols.
- Encryption and Security: Tunneling protocols can be used to encrypt data and improve security during transmission, preventing unauthorized access to critical information.
Why protocol tunneling used by hackers?
Hackers use protocol tunneling for a variety of reasons, including:
- To circumvent security measures: Protocol tunneling can be used to circumvent firewalls and other network security restrictions. This can provide hackers access to networks and systems that they would not have had otherwise.
- To exfiltrate data: Protocol tunneling can be used to conceal data exfiltration from a network. This is due to the fact that the data is tunneled through a valid protocol, such as HTTPS or DNS, which is frequently not monitored by security systems.
- To establish command and control channels: Protocol tunneling can be used to establish command and control channels between a hacked system and the attacker’s command and control server. This enables the attacker to take control of the compromised system and issue commands.
- To disguise harmful activity: Protocol tunneling can be used to disguise malicious activity by masquerading it as legitimate communication. This can make it harder for security systems to identify and prevent assaults.
Here are some specific uses of protocol tunneling by hackers:
- DNS tunneling: DNS tunneling is a technique for tunneling traffic between two systems that uses the DNS protocol. This can be used to circumvent firewalls and other security measures, as well as to exfiltrate data.
- HTTP tunneling: HTTP tunneling is a mechanism for tunneling traffic between two systems that uses the HTTP protocol. This can also be used to circumvent firewalls and other security measures, as well as to exfiltrate data.
- ICMP tunneling: ICMP tunneling is a technique for tunneling traffic between two systems that employs the ICMP protocol. This can be used to circumvent firewalls and other security measures, as well as to establish command and control channels.
It’s crucial to realize that protocol tunneling isn’t always bad. It is a legal technique that can be used to connect to faraway networks and access resources that would otherwise be unavailable. Hackers, on the other hand, can exploit protocol tunneling to carry out nefarious actions.
Organizations can defend against protocol tunneling attacks by using a layered security strategy that comprises firewalls, intrusion detection systems (IDSs), and intrusion prevention systems (IPSs). They should also keep an eye out for unexpected traffic patterns and behavior on their networks.