The Shadow Brokers live upto their name and showed impact on Year 2017 where number of cyberattacks demonstrated What Could be Done with Leaked NSA executes on mass destruction level. The executes release medium explored and expanded from imgur, pastebin , twitter , Github to Steemit monthly subscribers service. Most of the code was designed and explored from network firewalls to get inside the computer systems of competitors like Russia, China, Iran to Windows / Linux / Swift Exploits which can havoc amount of compromise from User to Bank Levels. That, in turn, allows the N.S.A. to place “implants” in the system, which can lurk unseen for years and be used to monitor network traffic or enable a debilitating computer attack. The coding resembled a series of “products” developed inside the N.S.A.’s highly classified Tailored Access Operations unit, some of which were described in general terms in documents stolen three years ago by Edward J. Snowden, the former N.S.A. contractor now living in Russia. The impact caused mass destruction due to which world have seen lots of zero days emerged with Obvious ZERO DAY Impact Experience for lots of Organisations where they seen several departments went to Shut Down within a Day [ Remember 12 – 15 May Wannacry]. As per analysis on current trend lots of malwares used exploits and result was unprecedented destruction cost companies millions of loss to cover [ Fedex reported 300 Million loss due to ransomware attacks.
Shadow Brokers Debut : Equation Group – Cyber Weapons Auction
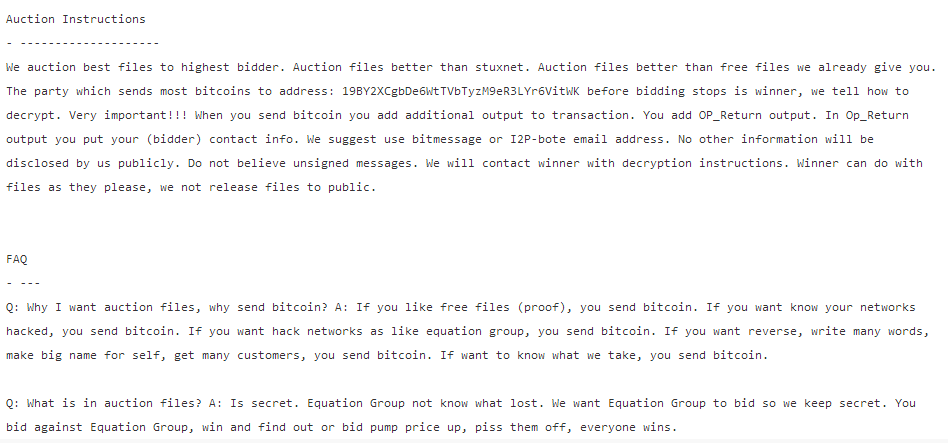
The first installment of executes release came up from Imgur, pastebin and twiiter account named EQGRP_Auction with the message
!!! Attention government sponsors of cyber warfare and those who profit from it !!!!
How much you pay for enemies cyber weapons? Not malware you find in networks. Both sides, RAT + LP, full state sponsor tool set? We find cyber weapons made by creators of stuxnet, duqu, flame. Kaspersky calls Equation Group. We follow Equation Group traffic. We find Equation Group source range. We hack Equation Group. We find many many Equation Group cyber weapons. You see pictures. We give you some Equation Group files free, you see. This is good proof no? You enjoy!!! You break many things. You find many intrusions. You write many words. But not all, we are auction the best files.
The reason specified by Shadow Brokers behind the leak as below:
Major Outbreaks and Causes so far
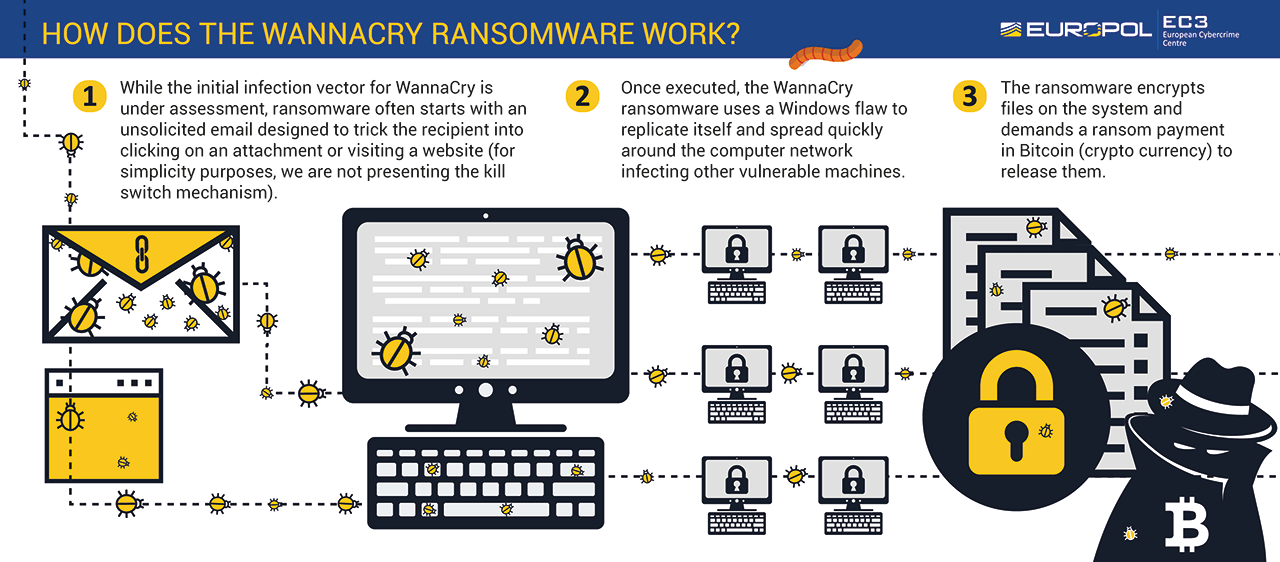
- WannaCry Ransomware Cyber Attack
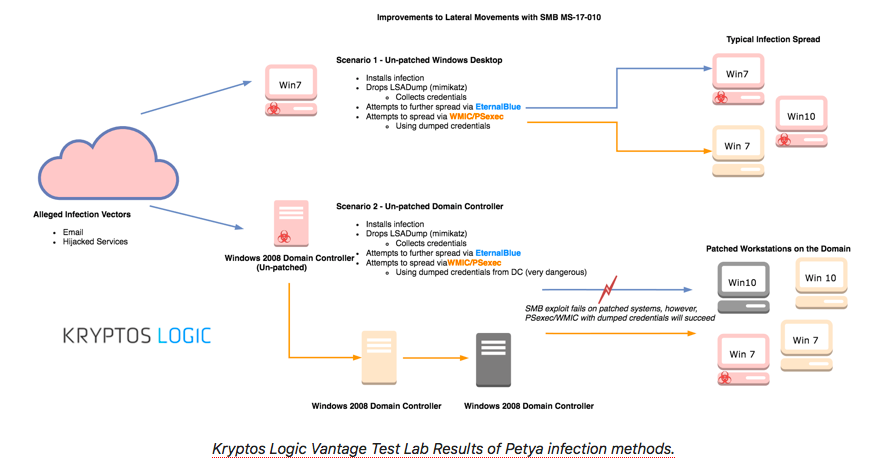
- Petya/ NoPetya Ransomware Cyber Attack
Shadow Brokers Leaks so far
- 13 August 2016: Equation Group Cyber Weapons Auction – Invitation
- eqgrp-auction-file.tar.xz.gpg – containing executes and implants for Linux and similar operating systems
- eqgrp-free-file.tar.xz.gpg – containing executes and implants for variety of networking equipments
- Repository Can be found at Github : EquationGroupLeak
- 20 October 2016: Message#5 — Trick or Treat?
- trickortreat.tar.xz.gpg” with a password of payus.
- 13 January 2017: MESSAGE FINALE
- equation_drug.tar.xz.gpg had been identified by Kaspersky AntiVirus as being Trojan.Win32.EquationDrug.
- Repository Can be found at Github : EquationGroupLeak/ equation_drug
- 8 April 2017: Don’t Forget Your Base
- eqgrp-auction-file.tar.xz.gpg – Linux executes and Implants
- Repository can be found at Github : EquationGroupLeak/ Linux
- 14 April 2017: Lost in Translation
- windows: contains Windows executes, implants and payloads
- swift: contains operational notes from banking attacks
- oddjob: docs related to the ODDJOB backdoor
- Repository can be found at Github : EQGRP_Lost_in_Translation
- 7 September 2017: TheShadowBrokers Dump Service – September 2017
- UNITEDRAKE, the implant is a “fully extensible remote collection system” that comes with a number of “plug-ins,” enabling attackers to remotely take full control over targeted Windows computers.
Leaked executes Datasheet
13 August 2016: Equation Group Cyber Weapons Auction – Invitation Source Equation-group-firewall-operations-catalogue
- EGREGIOUSBLUNDER A remote code execution executes for Fortigate firewalls that exploits a HTTP cookie overflow vulnerability. It affects models 60, 60M, 80C, 200A, 300A, 400A, 500A, 620B, 800, 5000, 1000A, 3600, and 3600A. The model of the firewall is detected by examining the ETag in the HTTP headers of the firewall. This is not CVE-2006-6493 as detected by Avast.
- ELIGIBLEBACHELOR An execute for TOPSEC firewalls running the TOS operation system, affecting versions 3.2.100.010, 3.3.001.050, 3.3.002.021 and 3.3.002.030. The attack vector is unknown but it has an XML-like payload that starts with <?tos length=”001e:%8.8x”?>.
- ELIGIBLEBOMBSHELL A remote code execution for TOPSEC firewalls that a HTTP cookie command injection vulnerability, affecting versions 3.2.100.010.1_pbc_17_iv_3 to 3.3.005.066.1. Version detection by ETag examination.
- WOBBLYLLAMA A payload for the ELIGIBLEBOMBSHELL TOPSEC firewall execute affecting version 3.3.002.030.8_003.
- FLOCKFORWARD A payload for the ELIGIBLEBOMBSHELL TOPSEC firewall execute affecting version 3.3.005.066.1.
- HIDDENTEMPLE A payload for the ELIGIBLEBOMBSHELL TOPSEC firewall execute affecting version tos_3.2.8840.1.
- CONTAINMENTGRID A payload for the ELIGIBLEBOMBSHELL TOPSEC firewall execute affecting version tos_3.3.005.066.1.
- GOTHAMKNIGHT A payload for the ELIGIBLEBOMBSHELL TOPSEC firewall execute affecting version 3.2.100.010.8_pbc_27. Has no BLATSTING support.
- ELIGIBLECANDIDATE A remote code execution execute for TOPSEC firewalls that exploits a HTTP cookie command injection vulnerability, affecting versions 3.3.005.057.1 to 3.3.010.024.1.
- ELIGIBLECONTESTANT A remote code execution execute for TOPSEC firewalls that execute a HTTP POST paramter injection vulnerability, affecting versions 3.3.005.057.1 to 3.3.010.024.1. This exploit can be tried after ELIGIBLECANDIDATE.
- EPICBANANA A privilege escalation execute against Cisco Adaptive Security Appliance (ASA) and Cisco Private Internet eXchange (PIX) devices. Exploitation takes advantage of default Cisco credentials (password: cisco). Affects ASA versions 711, 712, 721, 722, 723, 724, 80432, 804, 805, 822, 823, 824, 825, 831, 832 and PIX versions 711, 712, 721, 722, 723, 724, 804.
- ESCALATEPLOWMAN A privilege escalation execute against WatchGuard firewalls of unknown versions that injects code via the ifconfig command.
- EXTRABACON A remote code execution execute against Cisco Adaptive Security Appliance (ASA) devices affecting ASA versions 802, 803, 804, 805, 821, 822, 823, 824, 825, 831, 832, 841, 842, 843, 844. It exploits an overflow vulnerability using the Simple Network Management Protocol (SNMP) and relies on knowing the target’s uptime and software version.
- BOOKISHMUTE An execute against an unknown firewall using Red Hat 6.0.
- FALSEMOREL Allows for the deduction of the “enable” password from data freely offered by an unspecified firewall (likely Cisco) and obtains privileged level access using only the hash of the “enable” password. Requires telnet to be installed on the firewall’s inside interface.
Implants
- BLATSTING A firewall software implant that is used with EGREGIOUSBLUNDER (Fortigate) and ELIGIBLEBACHELOR (TOPSEC).
- BANANAGLEE A non-persistent firewall software implant for Cisco ASA and PIX devices that is installed by writing the implant directly to memory. Also mentioned in the previously leaked NSA ANT catalogue.
- BANANABALLOT A BIOS module associated with an implant (likely BANANAGLEE).
- BEECHPONY A firewall implant that is a predecessor of BANANAGLEE.
- JETPLOW A firmware persistence implant for Cisco ASA and PIX devices that persists BANANAGLEE. Also mentioned in the previously leaked NSA ANT catalogue.
- SCREAMINGPLOW Similar to JETPLOW.
- BARGLEE A firewall software implant for Juniper NetScreen firewalls.
- BUZZDIRECTION A firewall software implant for Fortigate firewalls.
- FEEDTROUGH A technique for persisting BANANAGLEE and ZESTYLEAK implants for Juniper NetScreen firewalls. Also mentioned in the previously leaked NSA ANT catalogue.
- JIFFYRAUL A module loaded into Cisco PIX firewalls with BANANAGLEE.
- BANNANADAIQUIRI An implant associated with SCREAMINGPLOW. Yes, banana is spelled with three Ns this time.
- POLARPAWS A firewall implant. Unknown vendor.
- POLARSNEEZE A firewall implant. Unknown vendor.
- ZESTYLEAK A firewall software implant for Juniper NetScreen firewalls that is also listed as a module for BANANAGLEE. Also mentioned in the previously leaked NSA ANT catalogue.
- SECONDDATE A packet injection module for BANANAGLEE and BARGLEE.
- BARPUNCH A module for BANANAGLEE and BARGLEE implants.
- BBALL A module for BANANAGLEE implants.
- BBALLOT A module for BANANAGLEE implants.
- BBANJO A module for BANANAGLEE implants.
- BCANDY A module for BANANAGLEE implants.
- BFLEA A module for BANANAGLEE implants.
- BMASSACRE A module for BANANAGLEE and BARGLEE implants.
- BNSLOG A module for BANANAGLEE and BARGLEE implants.
- BPATROL A module for BANANAGLEE implants.
- BPICKER A module for BANANAGLEE implants.
- BPIE A module for BANANAGLEE and BARGLEE implants.
- BUSURPER A module for BANANAGLEE implants.
- CLUCKLINE A module for BANANAGLEE implants.
Tools
- BILLOCEAN Retrieves the serial number of a firewall, to be recorded in operation notes. Used in conjunction with EGREGIOUSBLUNDER for Fortigate firewalls.
- FOSHO A Python library for creating HTTP execute.
- BARICE A tool that provides a shell for installing the BARGLEE implant.
- DURABLENAPKIN A tool for injecting packets on LANs.
- BANANALIAR A tool for connecting to an unspecified implant (likely BANANAGLEE).
- PANDAROCK A tool for connecting to a POLARPAWS implant.
- TURBOPANDA A tool that can be used to communicate with a HALLUXWATER implant. Also mentioned in the previously leaked NSA ANT catalogue.
- TEFLONDOOR A self-destructing post-execution shell for executing an arbitrary file. The arbitrary file is first encrypted with a key.
- 1212/DEHEX Converts hexademical strings to an IP addresses and ports.
- XTRACTPLEASING Extracts something from a file and produces a PCAP file as output.
- NOPEN A post-execution shell consisting of a client and a server that encrypts data using RC6. The server is installed on the target machine.
- BENIGNCERTAIN A tool that appears to be for sending certain types of Internet Key Exchange (IKE) packets to a remote host and parsing the response.
14 April 2017: Lost in Translation Source : Published at Bleeping Computer and blog.barkly.com
- EASYBEE appears to be an MDaemon email server vulnerability [source, source, source]
- EASYPI is an IBM Lotus Notes execution [source, source] that gets detected as Stuxnet [source]
- EWOKFRENZY is an execute for IBM Lotus Domino 6.5.4 to 7.0.2 [source, source]
- EXPLODINGCAN is an IIS 6.0 execute that creates a remote backdoor [source, source]
- ETERNALROMANCE is a SMBv1 execute over TCP port 445 which targets XP, 2003, Vista, 7, Windows 8, 2008, 2008 R2, and gives SYSTEM privileges [source, source]
- EDUCATEDSCHOLAR is a SMB execute [source, source]
- EMERALDTHREAD is a SMB execute for Windows XP and Server 2003 [source, source]
- EMPHASISMINE is a remote IMAP execute for IBM Lotus Domino [source, source]
- ENGLISHMANSDENTIST sets Outlook Exchange WebAccess rules to trigger executable code on the client’s side to send an email to other users [source, source]
- ERRATICGOPHER is a SMBv1 execute targeting Windows XP and Server 2003 [source, source]
- ETERNALSYNERGY is a SMBv3 remote code execution flaw for Windows 8 and Server 2012 [source, source, source]
- ETERNALBLUE is a SMBv1 and SMBv2 execute [source]
- ETERNALCHAMPION is a SMBv1 execute [source]
- ESKIMOROLL is a Kerberos execute targeting 2000, 2003, 2008 and 2008 R2 domain controllers [source, source]
- ESTEEMAUDIT is an RDP execute and backdoor for Windows Server 2003 and Windows XP [source, source]
- ECLIPSEDWING is an RCE execute for the Server service in Windows Server 2008 and later [source, source]
- EXPANDINGPULLEY is another Windows implant [source]
- ETRE is an execute for IMail 8.10 to 8.22 [source]
The leak also contained the following hacking tools:
- FUZZBUNCH is an execute framework, similar to MetaSploit [source, source], which was also part of the December-January “Windows Tools” Shadow Brokers auction [source]
- DOUBLEPULSAR is a RING-0 multi-version kernel mode payload [source]
- PASSFREELY is a tool that bypasses authentication for Oracle servers [source]
- ODDJOB is an implant builder and C&C server that can deliver executes for Windows 2000 and later [source, source], also not detected by any AV vendors [source]
- GROK is a keylogger for Windows, also known about since Snowden [source]
Aftermath of Shadow Brokers Arise
Cyber Attacks via Shadow Brokers Leaks
- 18 Aug 2016 BENIGNCERTAIN Equation Group’s BENIGNCERTAIN tool – a remote executed to extract Cisco VPN private keys
- 19 August 2016 Researcher Grabs VPN Password With Tool From NSA Dump
- 16 January 2017 US-CERT Advisory urges admins to firewall off Windows SMB – Shadow Brokers may have loosed a zero-day so you’re better safe than sorry
- 19 January 2017 US-CERT – Warning, Shadow Brokers Hackers are offering an SMB Zero-Day execute
- 11 April 2017 EXTREMEPARR and EBBISLAND execution – Working remote root execution leaked in Shadow Brokers dump – x86, Sparc running Solaris 6-10 at risk.
- 14 April 2017 – ShadowBrokers: Exploit Leaks – swift, windows, oddjob
- 17 April 2017 – Hackers Reveal Apparent NSA Targeting of SWIFT Bureaus
- 17 April 2017 – SWIFT Media Statement – Shadow Brokers – Allegations surrounding attempts to gain unauthorised access to data at two service bureaux
- 19 April 2017 DOUBLEPULSAR and ETERNALBLUE Exploitation – From git clone to Pwned – Owning Windows with DoublePulsar and EternalBlue (Part 1),(Part2),(Part3)
- 21 April 2017 DOUBLEPULSAR and ETERNALBLUE Exploitation – Script kiddies pwn 1000s of Windows boxes using leaked NSA hack tools
- 22 April 2017 DOUBLEPULSAR and ETERNALBLUE Exploitation – Security researcher warn of hackers compromised thousands of Windows boxes using leaked NSA hack tools DOUBLEPULSAR and ETERNALBLUE
- 2 MAY 2017 Eternalromance Exploitation – Eternalromance: Exploiting Windows Server 2003
- 12 May 2017 ETERNALBLUE Exploitation – WannaCry Ransomware Statistics: The Numbers Behind the Outbreak
- 19 May 2017 ETERNALBLUE Exploitation – Two newly discovered hacking campaigns found exploiting SMB Flaw weeks before Wannacry
- 22 May 2017 ETERNALBLUE Exploitation At least 3 different groups have been leveraging the NSA EternalBlue exploit, what’s went wrong?
- 24 May 2017 Eternalblue Exploitation for Cryptocurrency – The State of EternalBlue Exploitation in the Wild
- 25 May 2017 EsteemAudit Exploitation – Wanna Cry Again? NSA’s Windows ‘EsteemAudit’ RDP Exploit Remains Unpatched
- 5 June 2017 Devastating Global ‘ExplodingCan’ Cyber Attack Is Imminent, Warns Experts
- 13 June 2017 ‘ExplodingCan’ NSA exploit menaces thousands of servers – Exploit Review
- 27 June 2017 Eternalblue Exploitation via Ransomware – A Petya Ransomware variant that uses the Eternalblue exploit starts from Ukraine and spreading quickly worldwide
- 27 June 2017 Eternalblue Exploitation via Ransomware – A massive cyberattack is hitting organisations around the world
- 21 September 2017 Eternal Exploitation via Banking Trojan – Retefe banking Trojan leverages EternalBlue exploit in Swiss campaigns
Malware Exploitation with leaked NSA Exploits embedded
- 12 May 2017 EternalBlue Exploitation via Ransomware An Analysis of the WannaCry Ransomware Outbreak by Mcafee Team
- 15 May 2017 EternalBlue/DoublePulsar Exploitation : Adylkuzz Cryptocurrency Mining Malware Spreading for Weeks Via EternalBlue/DoublePulsar
- 19 May 2017 EternalBlue Exploit Actively Used to Deliver Remote Access Trojans
- 20 May 2017 EternalBlue Exploitation via Ransomware – UIWIX, the Fileless Ransomware that leverages NSA EternalBlue Exploit to spread
- 2 June 2017 EternalBlue Exploitation via Trojan – Threat actors leverage EternalBlue exploit to deliver non-WannaCry payloads, this time to distribute Backdoor.Nitol and Trojan Gh0st RAT
- 15 June 2017 DoublePulsar Exploitation via Trojan – Trojan.BtcMine.1259 Trojan.DownLoader24.64313 –The malicious program designed for mining the Monero (XMR) cryptocurrency downloads the miner to a computer.
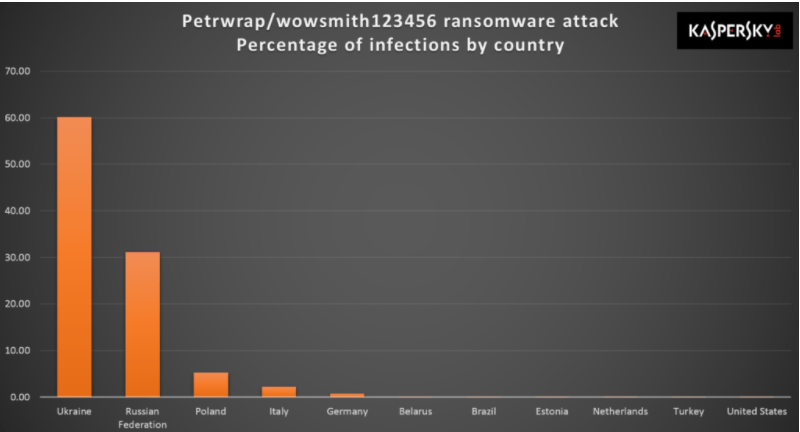
- 27 June 2017 EternalBlue Exploitation via Ransomware Petya ransomware outbreak Analysis : Petya ransomware impacting large organizations in multiple countries
- 27 July 2017 EternalBlue – New Version of “Trickbot” Adds Worm Propagation Module -The Trickbot gang appears to be testing a worm-like malware propagation module, which appears to spread locally via Server Message Block (SMB), scan domains for lists of servers via NetServerEnum Windows API, and enumerate other computers via Lightweight Directory Access Protocol (LDAP) enumeration.
- 21 August 2017 EternalBlue – Fileless cryptocurrency miner CoinMiner uses NSA EternalBlue exploit to spread
- 21 September 2017 EternalBlue – Retefe banking Trojan has historically targeted Austria, Sweden, Switzerland and Japan and banking sites in the United Kingdom since 2013. Now Added capabilities of EternalBlue exploit which downloads a PowerShell script from a remote server and itself includes an embedded executable that installs Retefe.
Shadow Brokers Leaked Exploits Analysis
- 17 August 2016 EGREGIOUSBLUNDER Fortigate Remote Code Execution
- 19 April 2017 DoublePulsar ANALYZING THE DOUBLEPULSAR KERNEL DLL INJECTION TECHNIQUE
- 21 April 2017 DoublePulsar DoublePulsar Initial SMB Backdoor Ring 0 Shellcode Analysis
- 11 May 2017 Esteemaudit A Deep Analysis by Fortinet Team
- 16 May 2017 Ethernalblue WANACRYPT0R RANSOMWORM Analysis
- 18 May 2017 WCry Ransomware Analysis by Secureworks team
- 23 May 2017 WannaCry Malware Profile by Fireeye team
- 4 June 2017 Eternalblue Memory analysis
- 27 June 2017 Petya Ransomware Analysis by Symantec team
- 27 June 2017 Petya Ransomware Analysis by Microsoft team
- 28 June 2017 Petya Ransomware Analysis by Kaspersky Lab
- 29 June 2017 EternalChampion Exploit Analysis
- 13 July 2017 EternalSynergy Exploitation Analysis
- 20 July 2017 EnglishmansDentist Exploit Analysis
- 18th September 2017 EXPLODINGCAN A VULNERABILITY REVIEW
Exploits Github Repositories
- Browsable content of eqgrp-auction-file.tar.xz
- Fortigate Firewalls – ‘EGREGIOUSBLUNDER’ Remote Code Execution
- Esteemaudit RDP Exploit leaked from Equationgroup (NSA) Esteemaudit-Metasploit
- Exploit-db : HOW TO EXPLOIT ETERNALBLUE TO GET A METERPRETER SESSION ON WINDOWS SERVER 2012 R2
- Eternal scanner is an network scanner for Eternal Blue exploit CVE-2017-0144
- MS17-010 Windows SMB RCE — exploits, payloads, and scanners
- WannaCry|WannaDecrypt0r NSA-Cyberweapon-Powered Ransomware Worm
Exploits Detection Repositories and Attacks POCs
- Fortinet Firewall EGREGIOUSBLUNDER Checker
- Fortinet FortiOS Web Interface Cookie Parser RCE (EGREGIOUSBLUNDER)
- MS17-010 SMB RCE Detection
- Doublepulsar-detection-script
- Hacking Tutorials – Exploiting Eternalblue for shell with Empire & Msfconsole
Infected / Affected Organizations
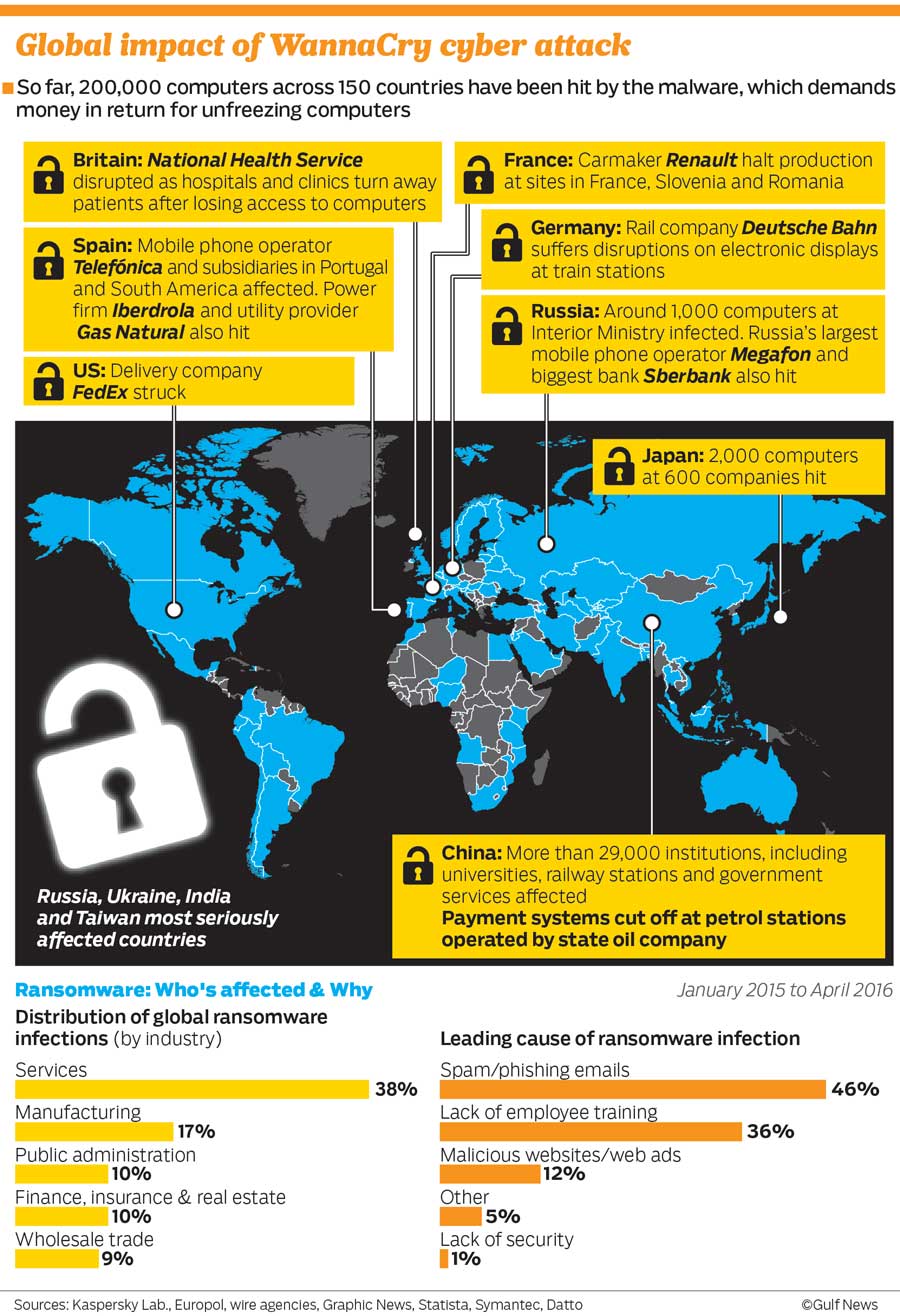
12 May 2017 ETERNALBLUE Exploitation – WannaCry Ransomware Statistics: The Numbers Behind the Outbreak
Source : WannaCry|WannaDecrypt0r
- NHS (uk) turning away patients, unable to perform x-rays. (list of affected hospitals)
- Nissan (uk) – Source
- Telefonica (spain) – Source
- power firm Iberdrola and Gas Natural (spain)
- FedEx (us) – Source
- University of Waterloo (ontario canada)
- Russia interior ministry & Megafon (russia) – Source
- VTB (russian bank) – Source
- Russian Railroads (RZD) – Source
- Portugal Telecom
- Сбербанк – Sberbank Russia (russia)
- Shaheen Airlines (pakistan, claimed on twitter)
- Train station in frankfurt (germany)
- Neustadt station (germany)
- the entire network of German Rail seems to be affected (@farbenstau)
- in China secondary schools and universities had been affected (source)
- A Library in Oman (@99arwan1)
- China Yanshui County Public Security Bureau – Source
- Renault (France) Source1 , Source2
- Schools/Education (France) – Source
- University of Milano-Bicocca (italy)
- A mall in singapore – Source
- ATMs in china – Source
- norwegian soccer team ticket sales-Source
- STC telecom (saudia arabia, more, more)
- All ATMs in india closed
- US radiology equipment – Source
- More at Wikipedia they seem to be cataloguing the infections faster/better.
27 June 2017 Petya Ransomware Global Outbreak – A massive cyberattack is hitting organisations around the world
- The global shipping and logistics firm Maersk — which is based in Denmark — confirmed that it was dealing with a intrusion affecting “multiple sites and business units.” – Source
- Russian oil company Rosneft said it was responding to “a massive hacker attack”- Source
- FedEx estimates ransomware attack cost $300 million – Source
- Aircraft manufacturer Antonov and two postal services
- A Pennsylvania hospital operator, Heritage Valley Health System, which reported its computer network was down, causing operations to be delayed – but it is not yet clear if it was subject to the same type of attack
- Reckitt Benckiser sales take a knock after crippling cyber attack and Published Statement to customers
- Netherlands-based shipping company TNT, which said some of its systems needed “remediation”
- French construction materials company St Gobain
- US pharmaceuticals-maker Merck Sharp & Dohme
- The local offices of the law firm DLA Piper – a sign in the firm’s Washington DC office said: “Please remove all laptops from docking stations and keep turned off – no exceptions.”
