There are a number of Live Maps that track Ransomware and Cyber Attacks around the world. These maps can be a valuable resource for organizations that are trying to stay informed about the latest threats.
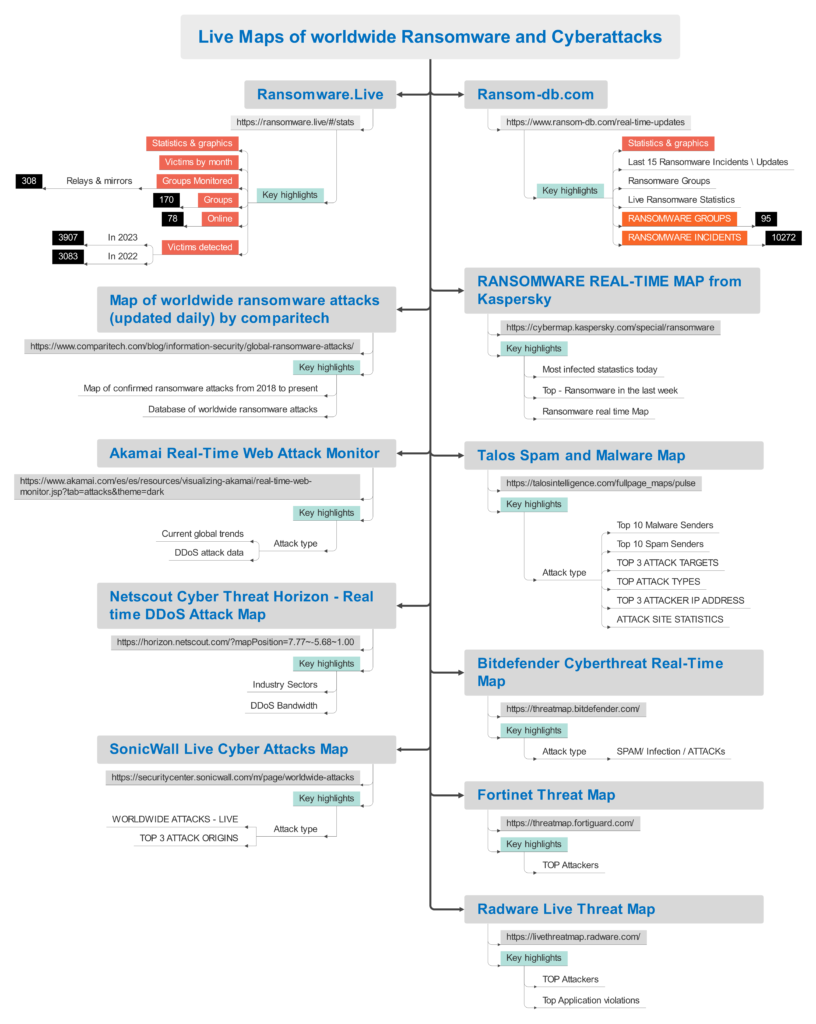
1. ransomware.live
The website ransomware.live is used to disseminate ransomware. A form of virus known as ransomware encrypts a victim’s files and demands payment in order to unlock them. Despite being a relatively new website, ransomware.live has already been used to disseminate malware from several different families, including Makop, LockBit, and Conti.
Key highlights:
- A relatively new website called ransomware.live is used to disseminate ransomware.
- Several other ransomware families, including Makop, LockBit, and Conti, have been distributed over the website.
- A statement on the website informs users that their files have been encrypted and that they must pay a ransom to unlock them.
- The website features a clock that displays the remaining time before the ransom is due.
- The victim’s files will be irreversibly erased if the ransom is not paid by the specified time.
- Paying the ransom is not recommended by experts because it just encourages the attackers to keep creating and disseminating ransomware.
- Keeping your software up to date and backing up your data is the greatest method to safeguard yourself from ransomware.
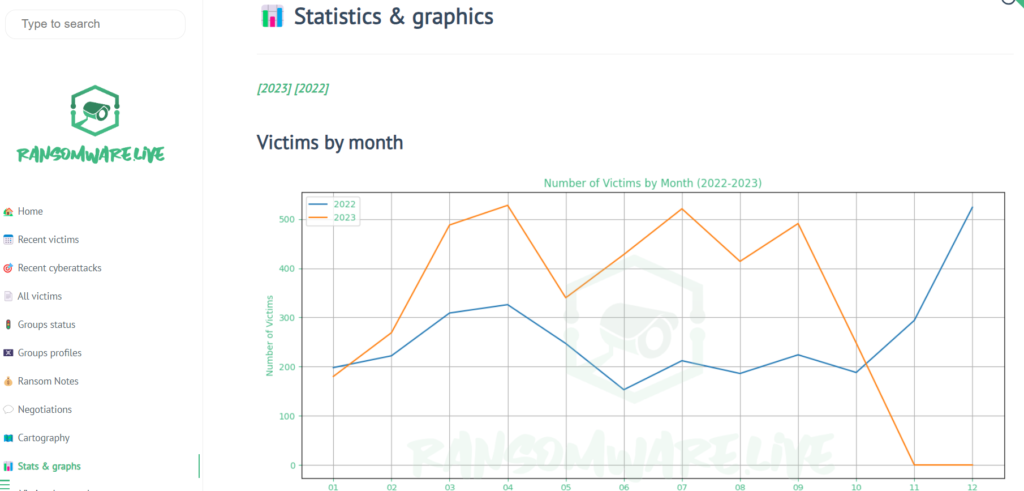
https://ransomware.live/#/stats
2. Ransom-DB
A website called Ransom-DB offers details about ransomware organizations and the people they have victimized. The website has a summary of current ransomware assaults as well as a searchable database of ransomware groups. The website also offers instructions on how to guard against ransomware.
Key highlights:
- Searchable database of ransomware groups
- List of recent ransomware attacks
- Information about how to protect yourself from ransomware
- Ransomware simulator
- Ransomware decryptor
- Ransomware intelligence feed
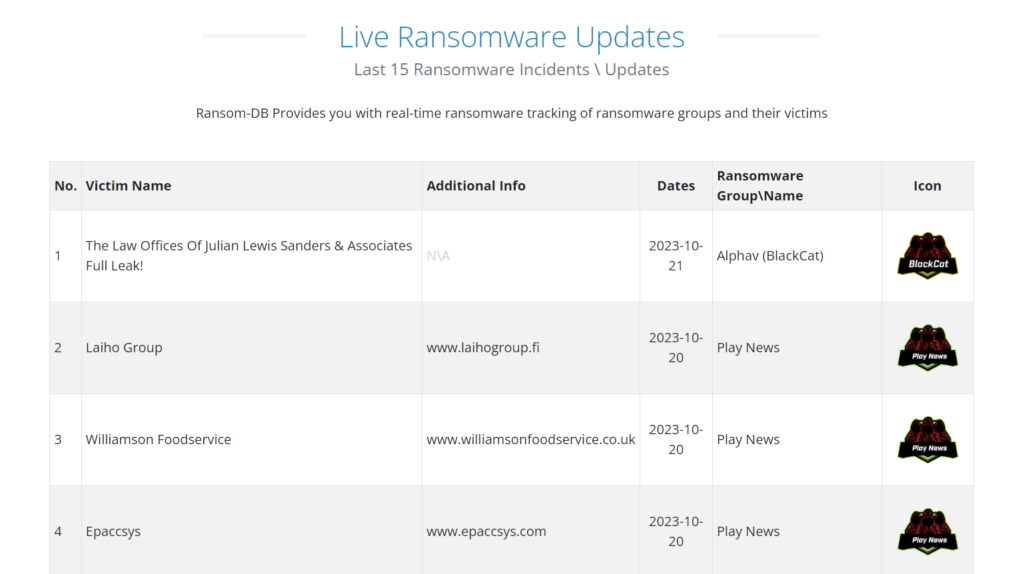
https://www.ransom-db.com/real-time-updates
3. RANSOMWARE REAL-TIME MAP from Kaspersky
A real-time map of ransomware assaults taking place worldwide is available from Kaspersky. The map displays each attack’s location, the type of ransomware employed, and the number of victims.
key highlights:
- Ransomware attacks are visible all around the world, according to the map.
- LockBit 2.0, Conti, and Hive are the three most popular varieties of ransomware.
- India, Brazil, and the United States are the top three nations impacted by ransomware.
- Attacks involving ransomware are increasing.
Most infected countries by ransomware today
- United States
- Brazil
- India
- Turkey
- Germany
Top – Ransomware in the last week
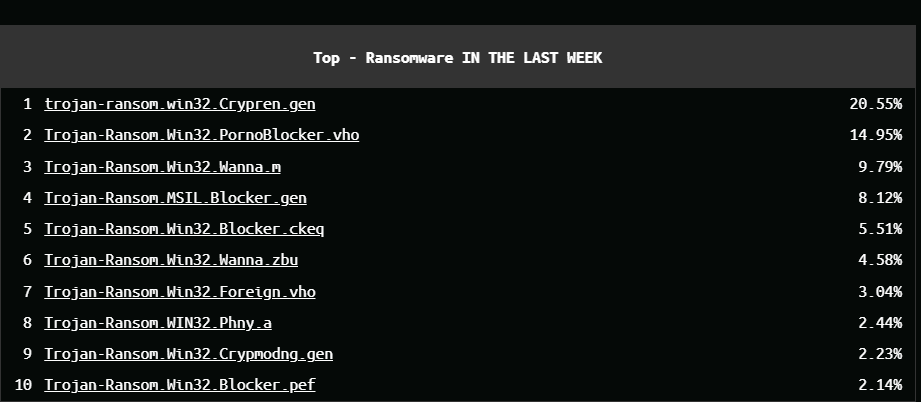
for more detailed: https://cybermap.kaspersky.com/special/ransomware
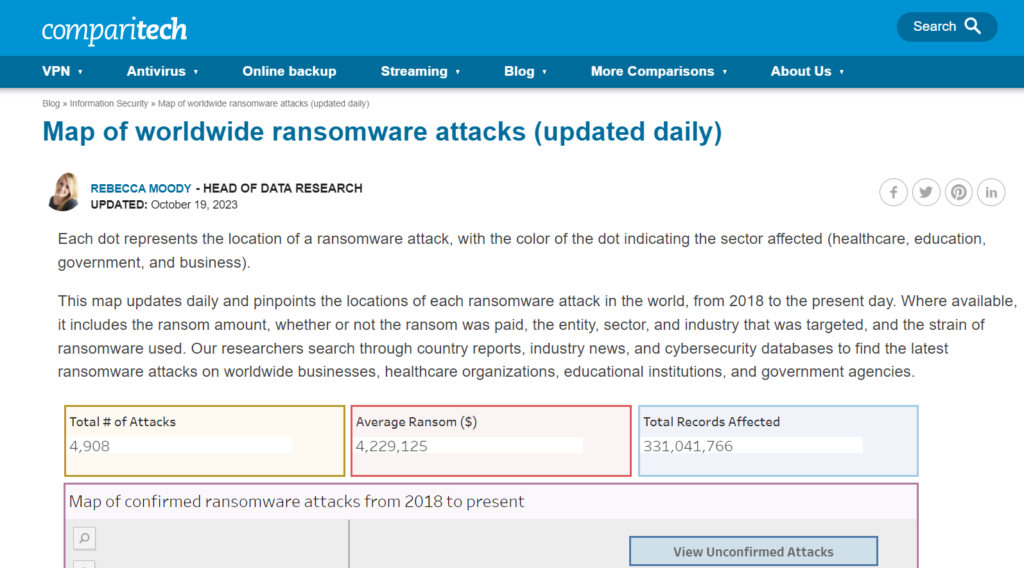
4. Map of worldwide ransomware attacks (updated daily) by comparitech
This map, which shows the locations of every ransomware attack worldwide from 2018 to the present, is updated every day. When accessible, it contains information about the demanded ransom, whether it was paid, the organization or sector that was attacked, the type of ransomware employed, and all of the above.
To uncover the most recent ransomware attacks on international corporations, healthcare organizations, educational institutions, and governmental agencies, Comparitech researchers scan through country reports, industry news, and cybersecurity databases.
Key highlights:
- Map of confirmed ransomware attacks from 2018 to present
- Database of worldwide ransomware attacks
https://www.comparitech.com/blog/information-security/global-ransomware-attacks/
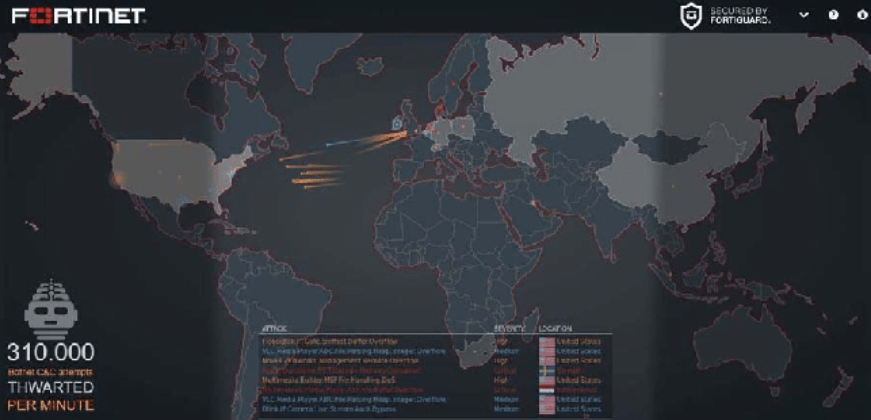
5. Fortinet Threat Map
The Fortinet Threat Map is a real-time display of information on worldwide threats gathered from the network of sensors that FortiGuard Labs has set up around the world. The most recent dangers, such as malware, botnets, and exploits, are shown on the globe as they are discovered. In order to see where threats are coming from and who they are targeting, users can filter the map by threat category, country, and region.
Key highlights:
- The map shows that threats are originating from all over the world.
- The most common threats are malware, botnets, and exploits.
- The United States, China, and Brazil are the top three countries where threats are originating.
- The number of threats is increasing.
https://threatmap.fortiguard.com/
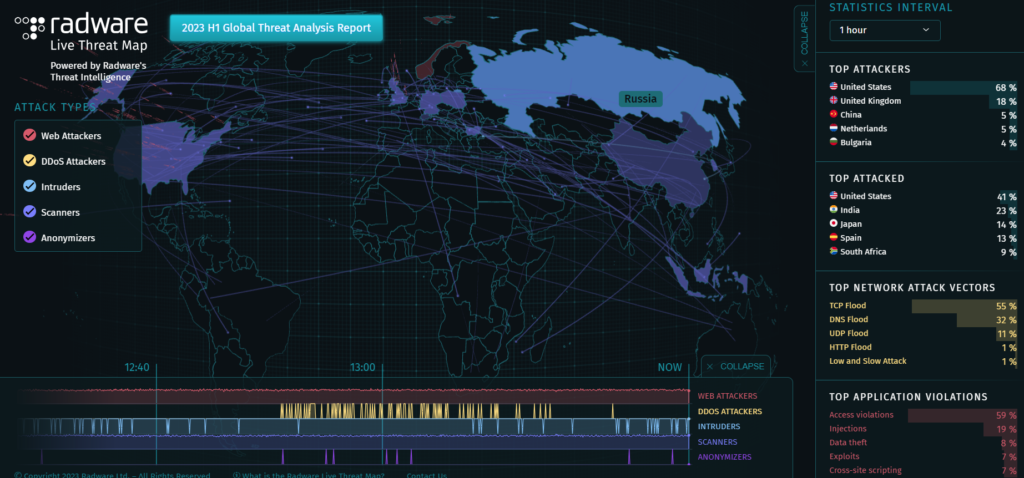
6. Radware Live Threat Map
The Radware Live Threat Map is a real-time display of information on worldwide threats gathered from Radware’s extensive network of sensors. The most recent dangers, such as DDoS attacks, web application attacks, and malware, are shown on the map as they are discovered. In order to see where threats are coming from and who they are targeting, users can filter the map by threat category, country, and region.
Key highlights:
- Threats are coming from all across the world, according to the map.
- DDoS attacks, online application attacks, and malware are the most frequent dangers.
- The top three nations from which threats are coming are the United States, China, and Russia.
- The quantity of hazards is growing.
https://livethreatmap.radware.com/
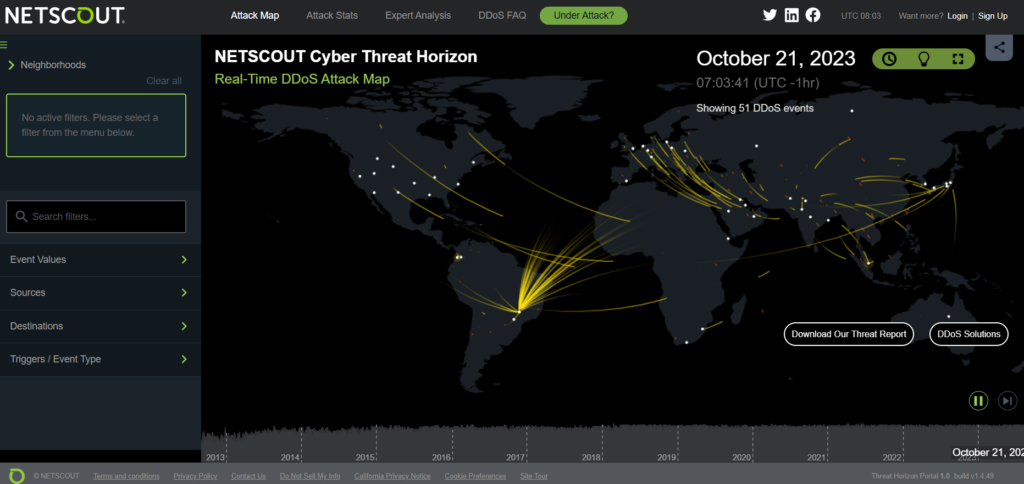
7. Netscout Cyber Threat Horizon – Real time DDoS Attack Map
For businesses who wish to stay up to date on the most recent DDoS threats, the Netscout Cyber Threat Horizon Real-time DDoS Attack Map is an invaluable resource. The map shows DDoS attacks as they are happening in real time around the globe. To view the origin and target of attacks, users can filter the map by attack type, country, and region.
https://horizon.netscout.com/?mapPosition=7.77~-5.68~1.00
8. Bitdefender Cyberthreat Real-Time Map
The Bitdefender Cyberthreat Real-Time Map presents current data on cyberthreats around the world that Bitdefender security solutions have identified.
The following details are shown on the map:
- Threat type: The specific kind of cyberthreat that was discovered, such as malware, phishing, or online attacks.
- Source: The nation where the danger first materialized.
- Target: The nation that the threat is aimed at.
- Threat count: The total number of threats found over the last 24 hours.
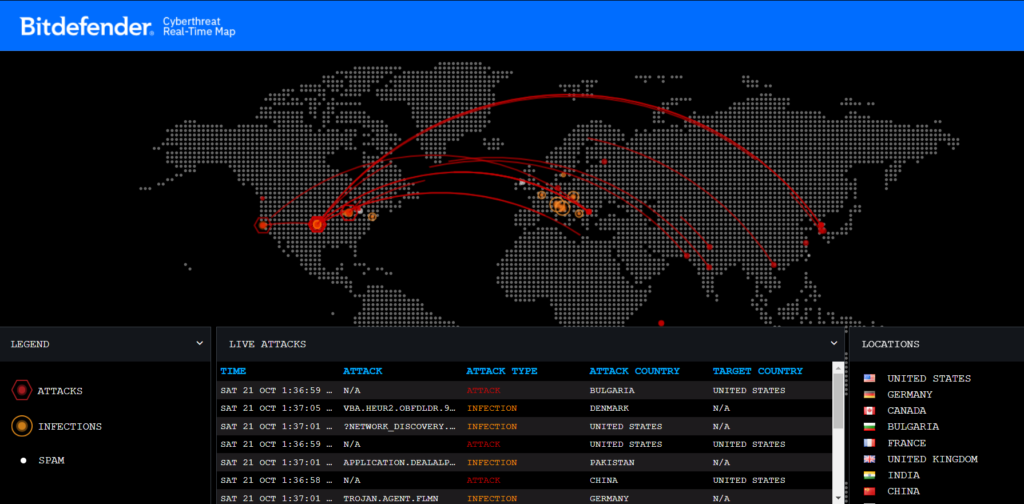
https://threatmap.bitdefender.com/
9. SonicWall Live Cyber Attacks Map
The SonicWall Live Cyber Attacks Map is updated by the SonicWall Capture Labs Threat Research Team. Global threat intelligence information gathered from SonicWall’s global network of sensors is displayed on this interactive map in real time. The most recent cyberattacks, including malware, botnets, and exploits, are displayed on the globe in real-time. In order to see where threats are coming from and who they are targeting, users can filter the map by threat category, country, and region.
Key highlights:
- Threats are coming from all across the world, according to the map.
- Malware, botnets, and exploits are the most prevalent types of threats.
- The top three nations from which threats are coming are the United States, China, and Russia.
- The quantity of hazards is growing.
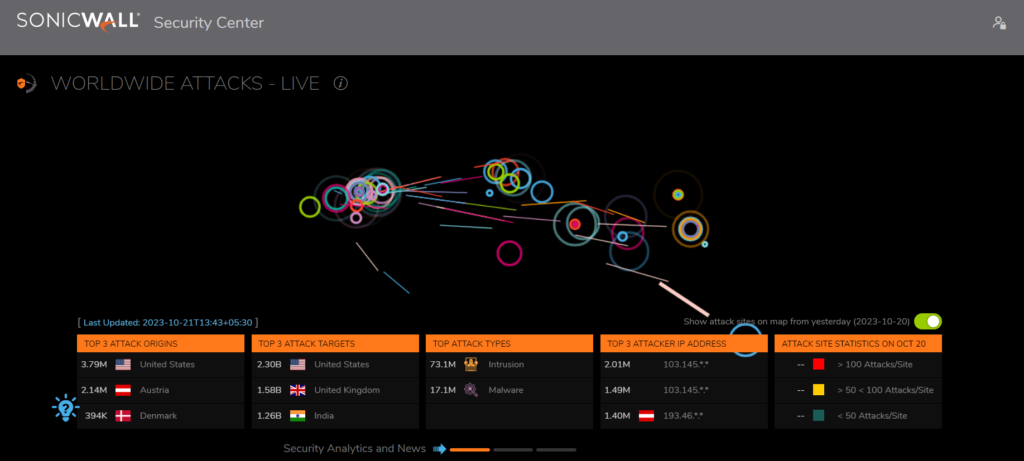
https://securitycenter.sonicwall.com/m/page/worldwide-attacks
10. Talos Spam and Malware Map
The Talos Spam and Malware Map is a live map that displays the most recent global spam and malware threats. Every 15 minutes, data from Cisco’s Talos Security Intelligence and Research Group is updated on the map.
Key highlights:
- Threats are coming from all across the world, according to the map.
- Malware and spam are the two most prevalent risks.
- The top three nations from which threats are coming are the United States, China, and Russia.
- The quantity of hazards is growing.
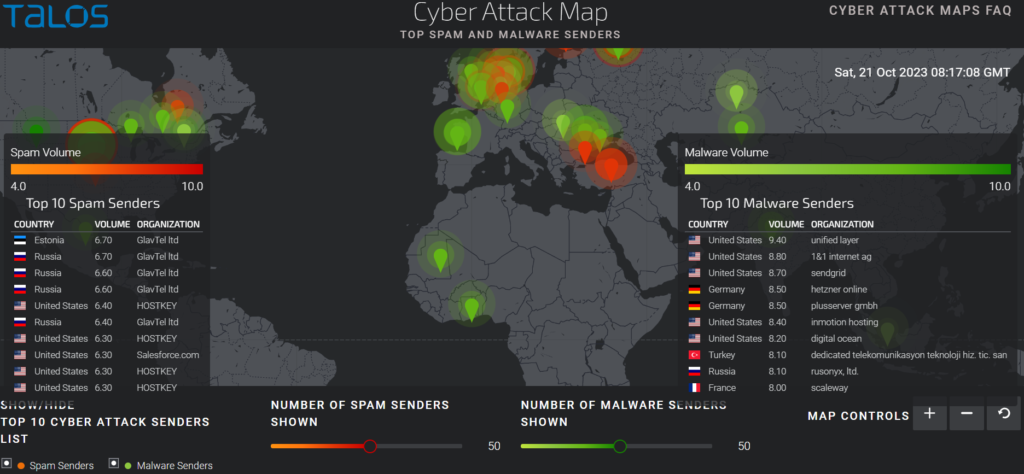
https://talosintelligence.com/fullpage_maps/pulse
11. Akamai Real-Time Web Attack Monitor
Organizations who wish to keep up with the most recent web attacks can benefit from using the Akamai Real-Time Web Attack Monitor. The monitor gives current information on worldwide web attacks that are taking place. To view the origin and target of attacks, users can filter the monitor by attack type, nation, and region.
Key highlights:
- The monitor demonstrates that web attacks are occurring anywhere in the world.
- SQL injection, cross-site scripting (XSS), and denial-of-service (DoS) assaults are the three most prevalent types of web attacks.
- The top three nations from which web attacks are coming are the United States, China, and Russia.
- Attacks on the web are becoming more frequent.
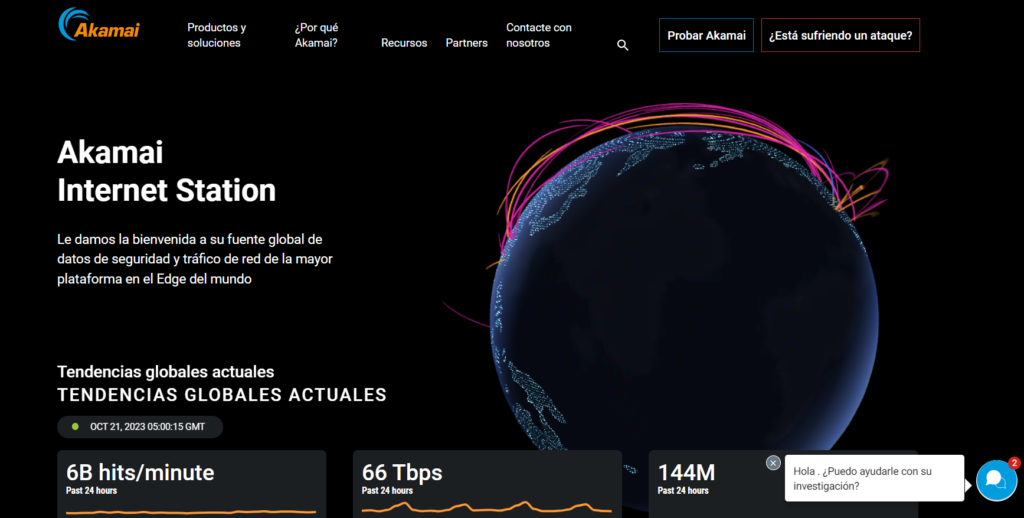
https://www.akamai.com/es/internet-station?tab=attacks&theme=dark
