Cyber Threat Intelligence
According to CERT-UK cyber threat intelligence (CTI) is an “elusive” concept. While cyber security comprises the recruitment of IT security experts, and the deployment of technical means, to protect an organization’s critical infrastructure, or intellectual property, CTI is based on the collection of intelligence using
- Open source intelligence (OSINT)
- Social media intelligence (SOCMINT)
- Human Intelligence (HUMINT)
- Dark Web Intelligence
CTI’s key mission is to research and analyze trends and technical developments in three areas:
- Cyber crime
- Cyber hactivism
- Cyber espionage (advanced persistent threat or APT)
Those accumulated data based on research and analysis enable states to come up with preventive measures in advance. Considering the serious impacts of cyber threats, CTI has been raised as an efficient solution to maintain international security.
Below are some of the selective which will help in Gathering Intelligence.
Emerging Threats is a collection point for a number of security projects, mostly related to Intrusion Detection and network Traffic Analysis like Suricata , SNORT® rules, firewall rules, and other IDS rulesets as some of them below:
- Known CompromisedHost List
- Dshield Top Attackers List (DshieldTopAttackers)
- Botnet Command and Control Server Rules (BotCC)
- Tor Exit Nodes List
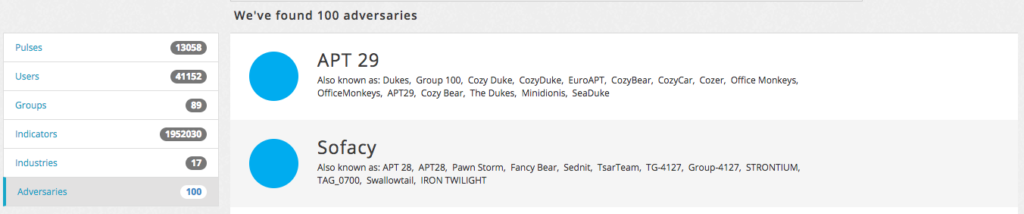
AlienVault Open Threat Exchange
Alienvault provides IOC collectives of APT, Malware, Cyber Espionage Activities, various threat exchanges and one of the best One Stop for getting intelligence.
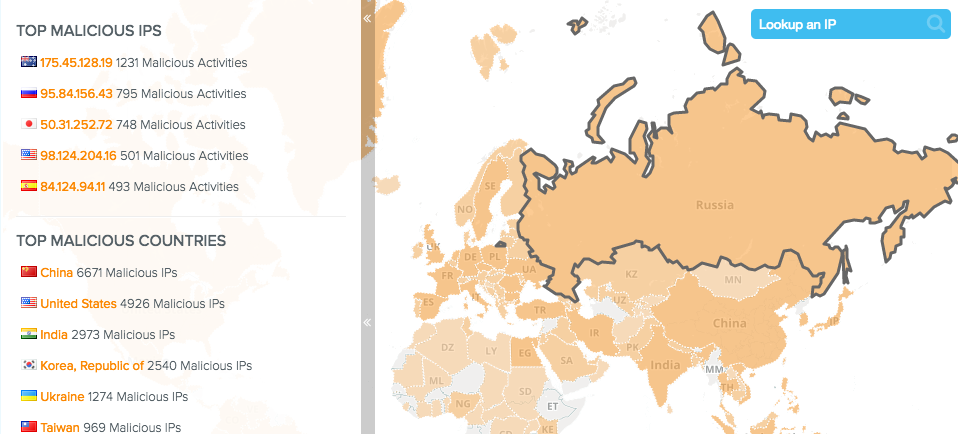
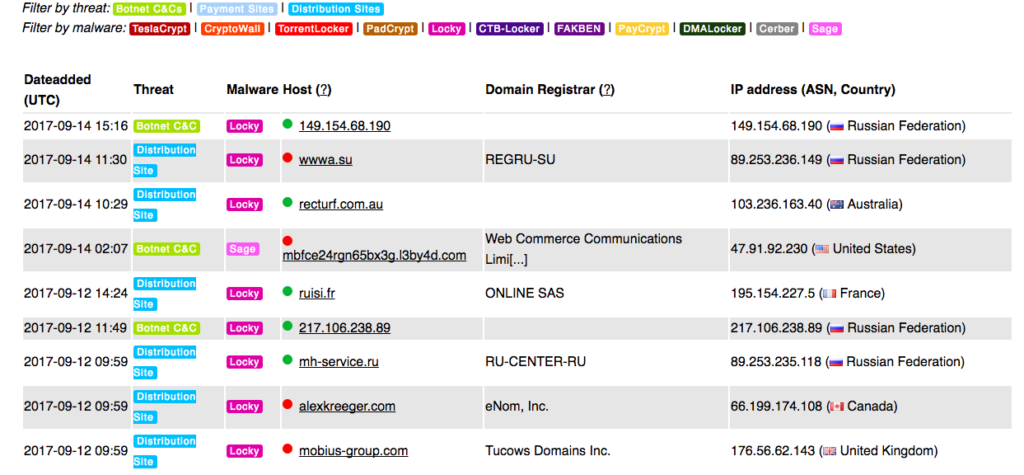
Abuse.ch provides one of the good malware tracker which includes intelligence for ZeuS / Ransomware families / Feodo which helps to track Command&Control servers (hosts) around the world and provides domain- and an IP-blocklist.

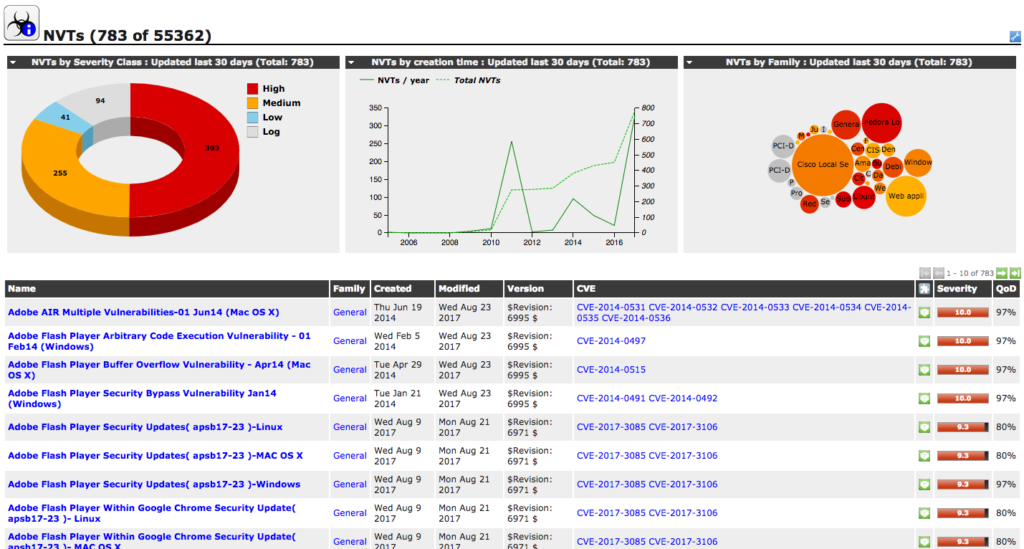
Openvas provides cumulative vulnerabilities view for recent exploits and related vulnerabilities which will help to focus on remediation implementations across orgwide.
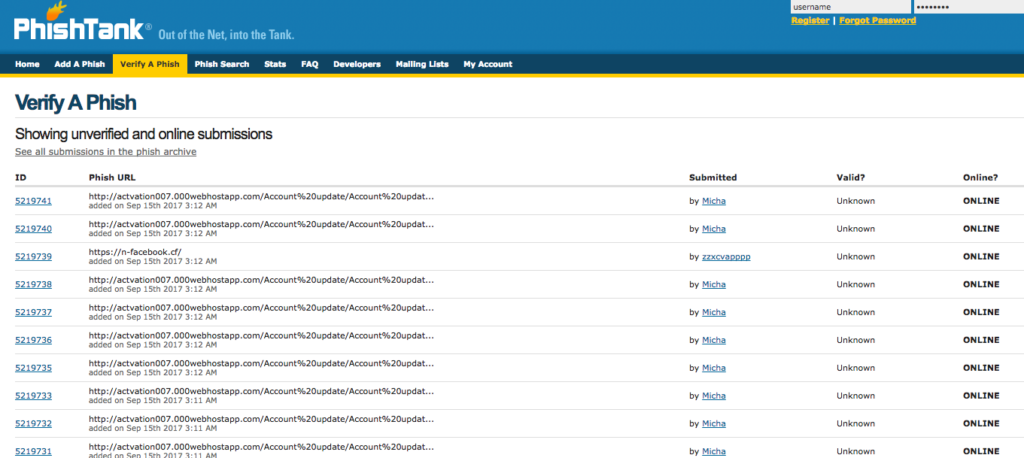
One of the good resource to search for Phishing Scams and collectives of phishing sites reported by security researchers worldwide. Also provides functionality to check suspected phishing link along with confirmed phishing sites.