What it is : Honeypot
In computer terminology, a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site, but is actually isolated and monitored, and that seems to contain information or a resource of value to attackers, who are then blocked. This is similar to police entrapment, colloquially known as “baiting,” a suspect
In other words it will be fooling trap for attacker by which all exploits whether 0-days or known are run against fake system and will produce samples to Analyze Attack.
Why to Use : Advanced and Unknown Attacks Analysis.
When Can be Used : User should set up External Honeypot which are Luring Attackers from Outside Corp Infra world and capture external threat actors or Internal Honeypots in which man-in-the-middle attacks, lateral movement worm activities, insider threats can be caught.
Some of the advantages can be achieved as :
- Gather forensic data without gathering legitimate traffic as well, creating smaller, high-value datasets.
- Waste attacker’s time by diverting attacks to a useless system, and get early warning about an attack.
- Does not require known attack signatures, unlike IDS’s.
- Some of the Honeypot Trends can be found here : DEF CON 23 – Packet Capture Village – Elliot Brink – Global Honeypot Trends
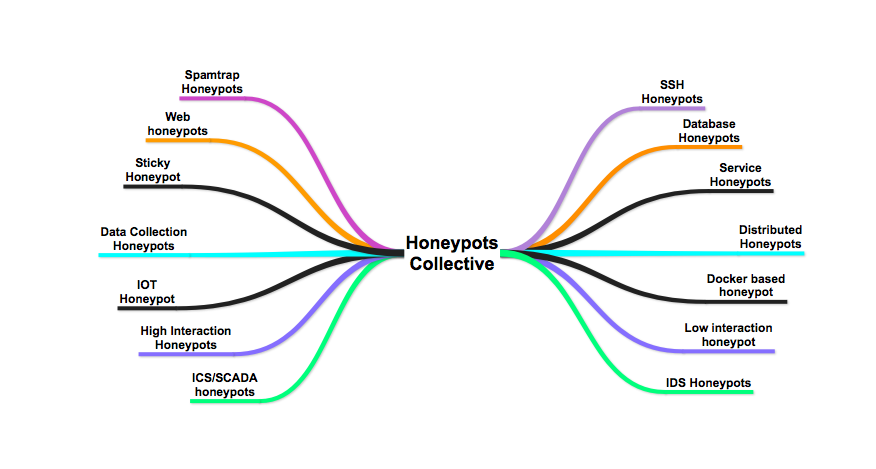
Database Honeypots
- Database Breach is one one of the biggest threat if occurred. It will cost vulnerable organization with Quantitative as well Qualitative risks due to years of gathered customers data got exposed with emails, social security numbers, personal information. Some of the recent infamous database breaches can be categorized as :
- Equifax Says Cyberattack May Have Affected 143 Million in the U.S. Equifax, one of the three major consumer credit reporting agencies, said on Thursday that hackers had gained access to company data that potentially compromised sensitive information for 143 million American consumers, including Social Security numbers and driver’s license numbers.
- Restaurant search website Zomato has announced that it has suffered a major security breach, resulting in the theft of a user database containing 17 million users’ names, email addresses and passwords.
- The hacking of a Kansas data system exposed the Social Security numbers (SSNs) of 5.5 million people from 10 states; data from another 805,000 people who didn’t share their SSNs was also compromised.
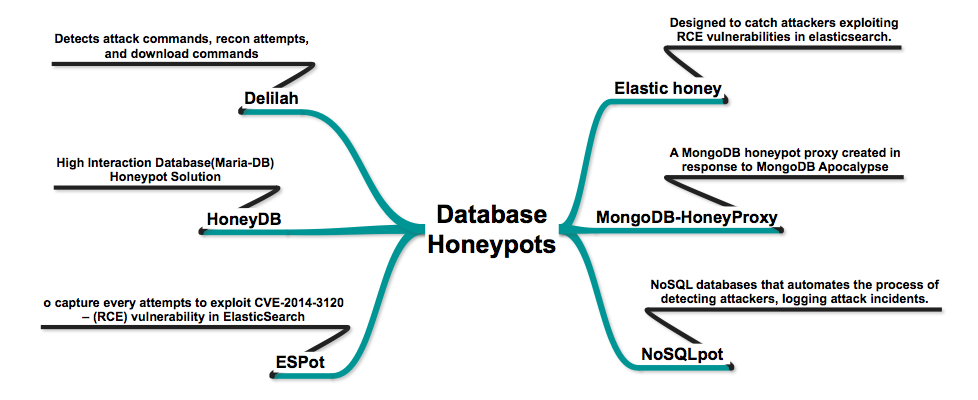
- MongoDB-HoneyProxy – A MongoDB honeypot proxy created in response to MongoDB Apocalypse as Ransom Attacks Hit 10,000 Servers.
- Elastic honey – Elastichoney is a simple elasticsearch honeypot designed to catch attackers exploiting RCE vulnerabilities in elasticsearch.
- HoneyDB – High Interaction Database(Maria-DB) Honeypot Solution
- NoSQLpot – The NoSQL Honeypot Framework, for NoSQL databases that automates the process of detecting attackers, logging attack incidents.
- ESPot – An Elasticsearch honeypot written in NodeJS, to capture every attempts to exploit CVE-2014-3120 – (RCE) vulnerability in ElasticSearch, exploitable by default on ElasticSearch prior to 1.2.0. The bug is found in the REST API, which does not require authentication, where the search function allows dynamic scripts execution
- Delilah – An Elasticsearch Honeypot written in Python – acts as a vulnerable Elasticsearch instance that detects and identifies attack commands, recon attempts, and download commands (specifically “wget” and “curl”)
Web Honeypots
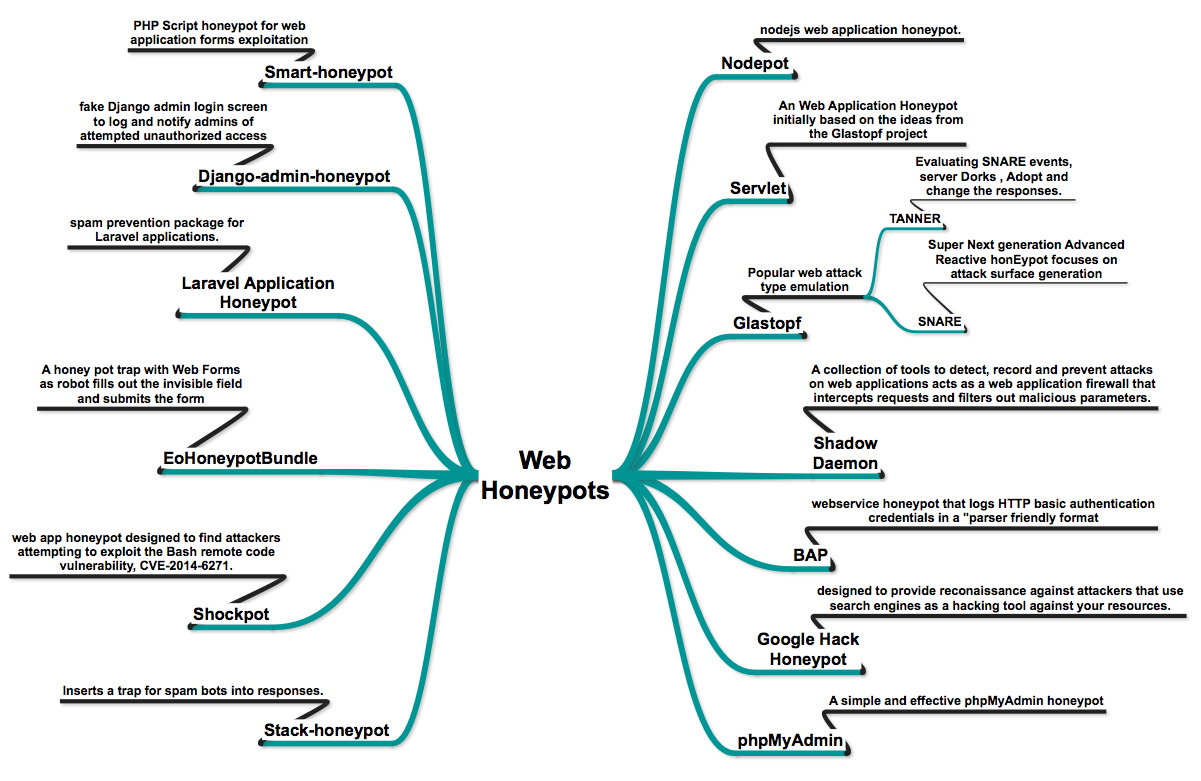
- Glastopf – Web Application Honeypot in which Popular attack type emulation is already in place like Remote File Inclusion via a build-in PHP sandbox, Local File Inclusion providing files from a virtual file system and HTML injection via POST requests.
- Snare/Tanner – successors to Glastopf
- phpmyadmin_honeypot – A simple and effective phpMyAdmin honeypot.
- servlet – Web application Honeypot.
- Nodepot – A nodejs web application honeypot.
- basic-auth-pot bap – http Basic Authentication honeypot.
- Shadow Daemon – A modular Web Application Firewall / High-Interaction Honeypot for PHP, Perl & Python apps.
- Servletpot – Web application Honeypot.
- Google Hack Honeypot – designed to provide reconnaissance against attackers that use search engines as a hacking tool against your resources.
- smart-honeypot – PHP Script demonstrating a smart honey pot.
- Bukkit Honeypot Honeypot – A honeypot plugin for Bukkit.
- Laravel Application Honeypot – Honeypot – Simple spam prevention package for Laravel applications.
- stack-honeypot – Inserts a trap for spam bots into responses.
- EoHoneypotBundle – Honeypot type for Symfony2 forms.
- shockpot – WebApp Honeypot for detecting Shell Shock exploit attempts.
- django-admin-honeypot – A fake Django admin login screen to notify admins of attempted unauthorized access.
WordPress Honeypots
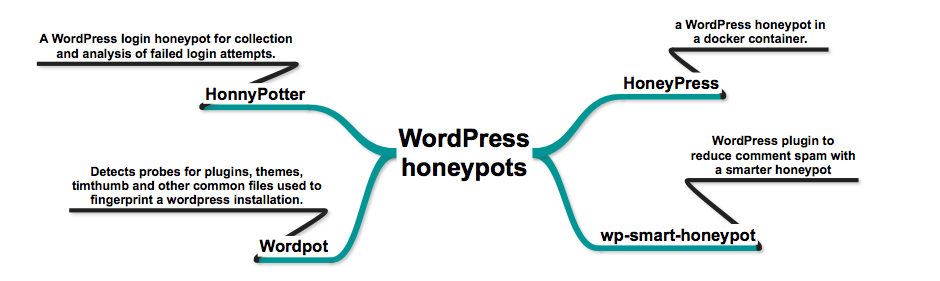
- HonnyPotter – A WordPress login honeypot for collection and analysis of failed login attempts.
- HoneyPress – python based WordPress honeypot in a docker container.
- wp-smart-honeypot – WordPress plugin to reduce comment spam with a smarter honeypot.
- wordpot – A WordPress Honeypot.
Service Honeypots
Service Honeypots essentially emulates various services like Printer Service , Camera Service, RDP Services , Webserver responding to Intel’s AMT platform which will attract attackers searching for specific services. These Honeypots can also capture IoT based attackers like Mirai, Perisirai botnets.
- honeyntp – NTP logger/honeypot.
- honeypot-camera – observation camera honeypot.
- troje – a honeypot built around lxc containers. It will run each connection with the service within a separate lxc container.
- HoneyPy – A low interaction honeypot.
- Ensnare – Easy to deploy Ruby honeypot.
- RDPy – A Microsoft Remote Desktop Protocol (RDP) honeypot in python.
- Honeyprint – Printer honeypot.
- Tom’s Honeypot – Low interaction Python honeypot.
- Honeyport – A simple honeyport written in Bash and Python.
- AMTHoneypot – Honeypot for Intel’s AMT Firmware Vulnerability CVE-2017-5689.
- Lyrebird – A modern high-interaction honeypot framework.
SSH Honeypots
- Kojoney
- Kojoney2 – low interaction SSH honeypot written in Python. Based on Kojoney by Jose Antonio Coret
- Kippo – Medium interaction SSH honeypot
- LongTail Log Analysis @ Marist College – analyzed SSH honeypot logs
- DRG SSH Username and Password Authentication Tag Clouds – live updated word clouds of SSH login honeypot data
- Cowrie – Cowrie SSH Honeypot (based on kippo)
- sshlowpot – Yet another no-frills low-interaction ssh honeypot in Go.
- sshhipot – High-interaction MitM SSH honeypot
- DShield docker – Docker container running cowrie with DShield output enabled.
- hornet – Medium interaction SSH Honeypot that supports multiple virtual hosts
- ssh-honeypot – Fake sshd that logs ip addresses, usernames, and passwords.
- Kippo_JunOS – Kippo configured to be a backdoored netscreen.
SMTP Honeypots
- Mailoney – SMTP honeypot, Open Relay, Cred Harvester written in python.
- Spamhole
- spamd
- Mail::SMTP::Honeypot – perl module that appears to provide the functionality of a standard SMTP server
- honeypot – The Project Honey Pot un-official PHP SDK
- SpamHAT – Spam Honeypot Tool
- SendMeSpamIDS.py Simple SMTP fetch all IDS and analyzer
- Shiva – Spam Honeypot with Intelligent Virtual Analyzer
Dockerized Honeypots
- Manuka – Docker based honeypot (Dionaea & Kippo).
- Dockerized Thug – A dockerized Thug to analyze malicious web content.
- Dockerpot – A docker based honeypot.
- Docker honeynet – Several Honeynet tools set up for Docker containers.
- mhn-core-docker – Core elements of the Modern Honey Network implemented in Docker.
Distributed Honeypots
- DemonHunter – Low interaction Honeypot Server.
- Smarthoneypot – custom honeypot intelligence system that is simple to deploy and easy to manage.
- Modern Honey Network – Multi-snort and honeypot sensor management, uses a network of VMs, small footprint SNORT installations, stealthy dionaeas, and a centralized server for management.
- ADHD – Active Defense Harbinger Distribution (ADHD) is a Linux distro based on Ubuntu LTS. It comes with many tools aimed at active defense preinstalled and configured.
- Distributed Web Honeypot Project