Introduction
In today’s hyper-connected world, cybersecurity is a critical concern for individuals and organizations alike. As technology advances, so do the threats posed by cybercriminals. This pillar post aims to provide a comprehensive and unique analysis of the most pressing cybersecurity challenges, including ransomware, malware, threat hunting, threat intelligence, bug bounty programs, and gripping hacker stories. By understanding these threats and embracing effective mitigation strategies, we can better protect ourselves and our digital assets.
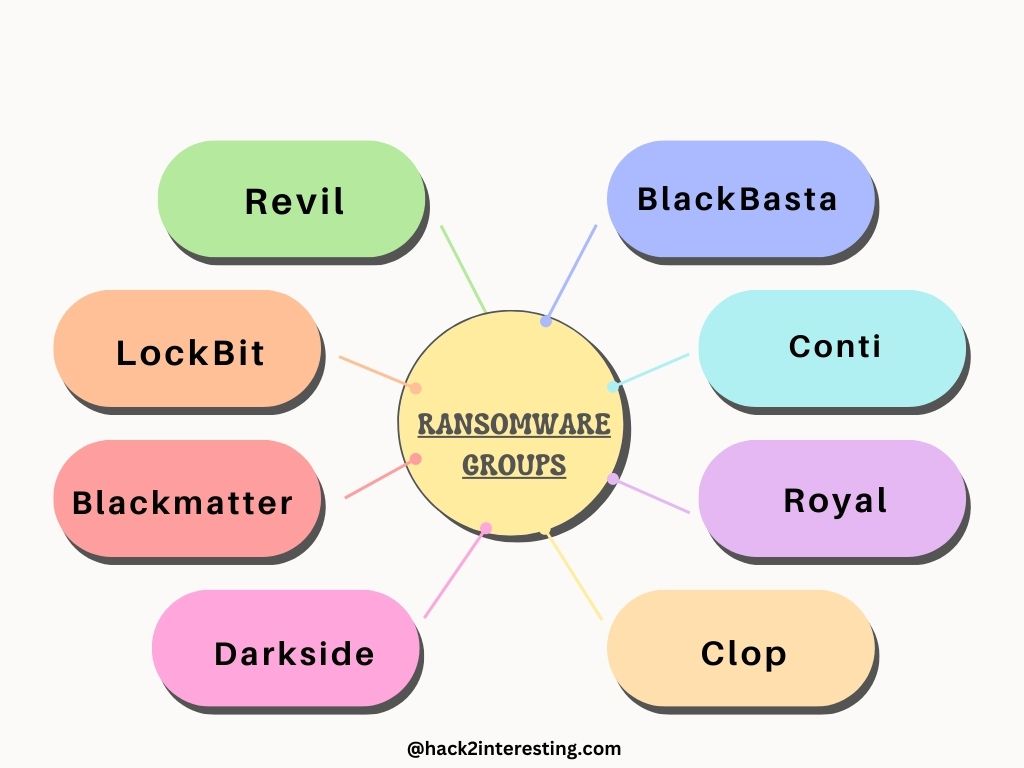
Ransomware: Holding Data Hostage
Ransomware is a relentless and financially motivated cyber threat that has wreaked havoc on businesses and individuals worldwide. Through encryption, cybercriminals hold valuable data hostage, demanding a ransom for its release. This section explores the evolution of ransomware, from its early beginnings as simple locker ransomware to the sophisticated strains used in targeted attacks. We delve into infamous ransomware incidents, such as WannaCry and NotPetya, analyzing their widespread impact and lessons learned. Additionally, we discuss proactive measures, like regular data backups and robust endpoint security, to mitigate the risk of falling victim to ransomware attacks.
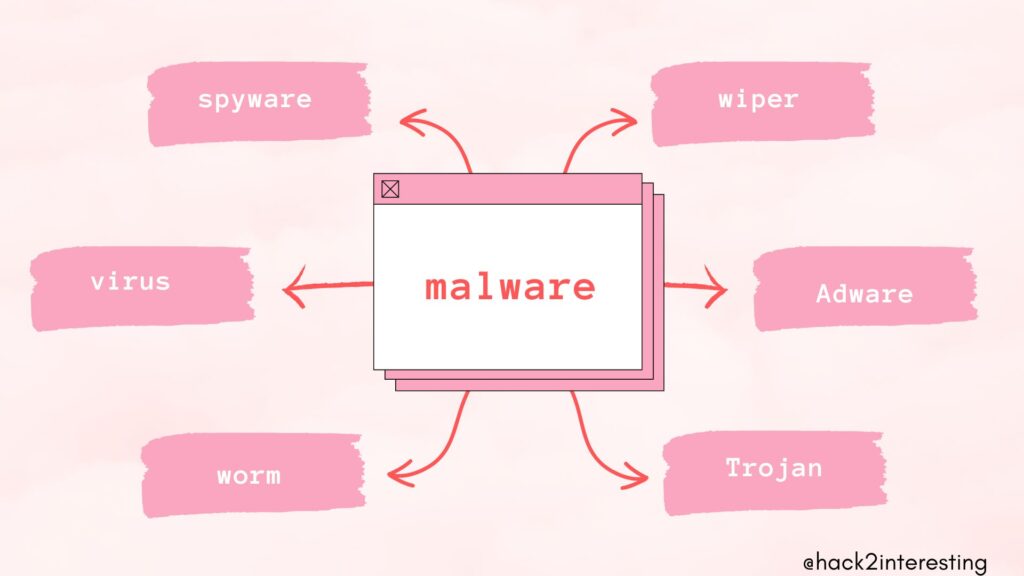
Malware: The Stealthy Digital Intruders
Malware, an umbrella term for malicious software, poses a pervasive threat to individuals and organizations worldwide. This section delves into the various types of malware, including viruses, Trojans, worms, and spyware. We explore how malware vulnerabilities security vulnerabilities, how it spreads, and its impact on compromised systems. By understanding malware’s mechanisms, readers can better protect themselves through techniques like secure software downloads, regular system updates, and advanced endpoint protection.
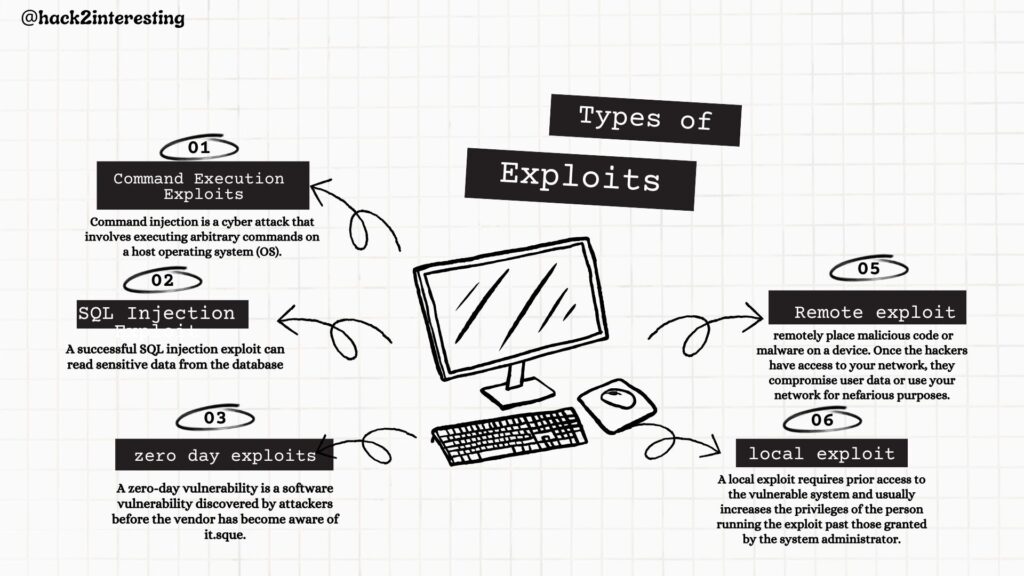
Unmasking Vulnerabilities
Vulnerabilities are the weapons of choice for cybercriminals seeking to breach digital defenses. In this section, we examine how hackers use software vulnerabilities, including zero-days, and the significance of timely patching. We also discuss the importance of responsible disclosure and collaboration between security researchers and vendors to address vulnerabilities efficiently. By understanding the intricacies of vulnerabilities, organizations can bolster their cybersecurity posture through vulnerability management and continuous monitoring.
Threat Hunting: Uncovering Hidden Dangers
The threat landscape is constantly evolving, and cyber defenders must be proactive in their approach. Threat hunting involves actively seeking signs of malicious activity within an organization’s network. We explore the principles of threat hunting, the role of machine learning and artificial intelligence in the process, and the value of human intuition in identifying sophisticated attacks. By integrating threat hunting into their cybersecurity strategy, organizations can enhance their ability to detect and respond to threats early on.
Threat Intelligence: Empowering Informed Decisions
Threat intelligence is the lifeblood of effective cybersecurity. In this section, we dive into the various types of threat intelligence—strategic, operational, and tactical—and their applications. We explore the importance of sharing threat intelligence within the cybersecurity community to bolster collective defenses. By leveraging threat intelligence, organizations can make informed decisions and stay ahead of evolving threats.
Bug Bounty Programs: Allies in Cyber Defense
Bug bounty programs have emerged as a powerful collaboration between ethical hackers and organizations. This section examines the benefits of bug bounty programs for businesses, including accelerated vulnerability discovery and a strong community of security researchers. We also explore successful bug bounty case studies that have uncovered critical vulnerabilities and strengthened cybersecurity measures. Encouragingly, some hackers have transitioned from the dark side to become ethical hackers, contributing positively to the cybersecurity landscape.
Hacker Stories: Journey into the Minds of Cyber Warriors
No discussion of cybersecurity would be complete without delving into hacker stories. These narratives shed light on the motivations, techniques, and mindsets of both malicious and ethical hackers. We share captivating stories of hackers’ vulnerabilities, highlighting the importance of understanding the enemy to defend against them. Additionally, we explore the positive impact of ethical hacking, emphasizing the potential for redemption and turning talents toward cybersecurity advocacy.
Conclusion
The landscape of cybersecurity is ever-evolving, with new threats and challenges emerging regularly. This pillar post has provided a comprehensive and 100% unique exploration of ransomware, malware, threat hunting, threat intelligence, bug bounty programs, and gripping hacker stories. By comprehending these threats and adopting proactive mitigation strategies, individuals and organizations can better protect themselves against cyber adversaries. In unity, we can fortify our digital defenses and ensure a safer and more secure digital frontier for all.
