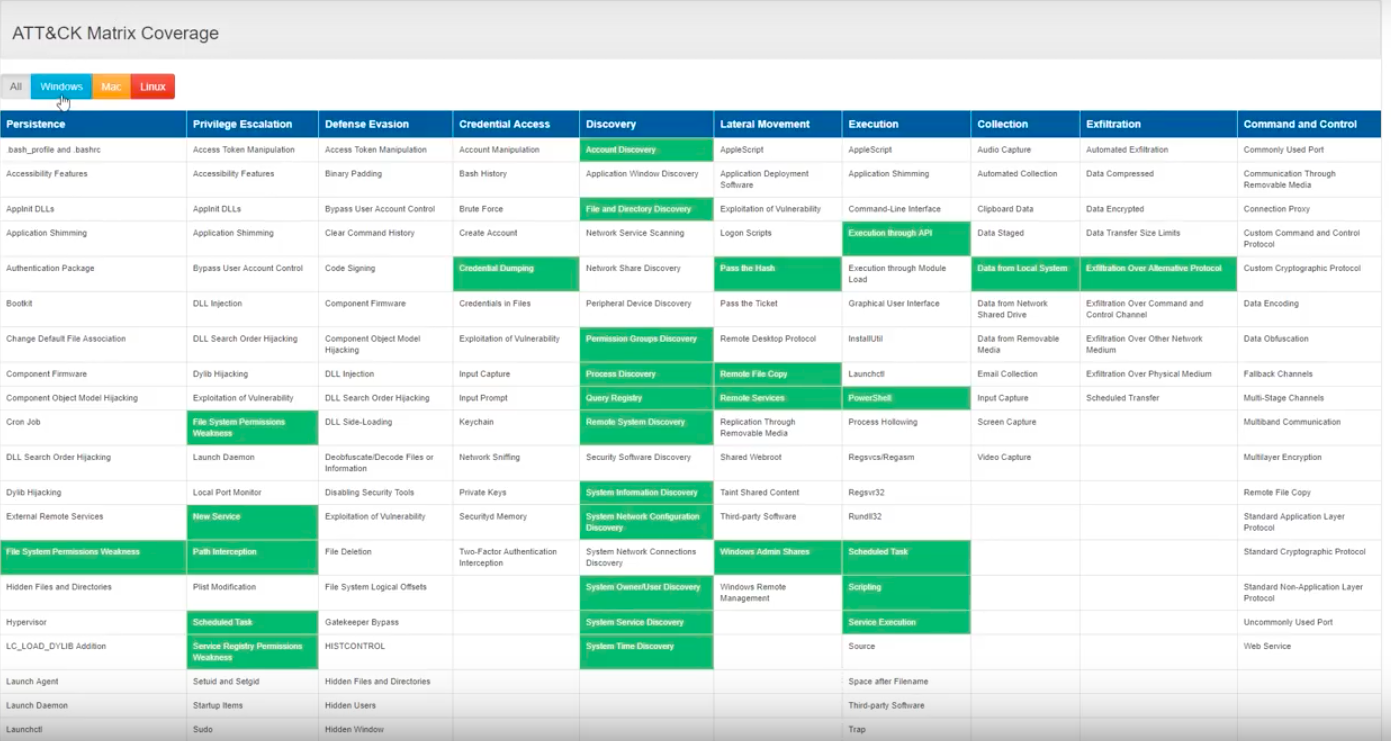
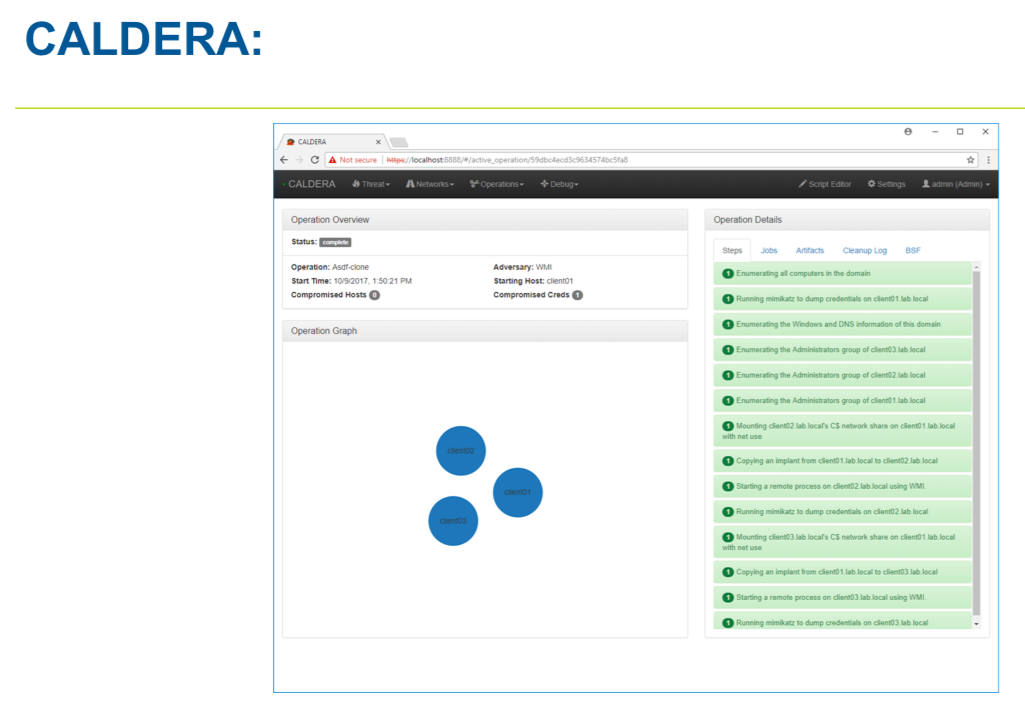
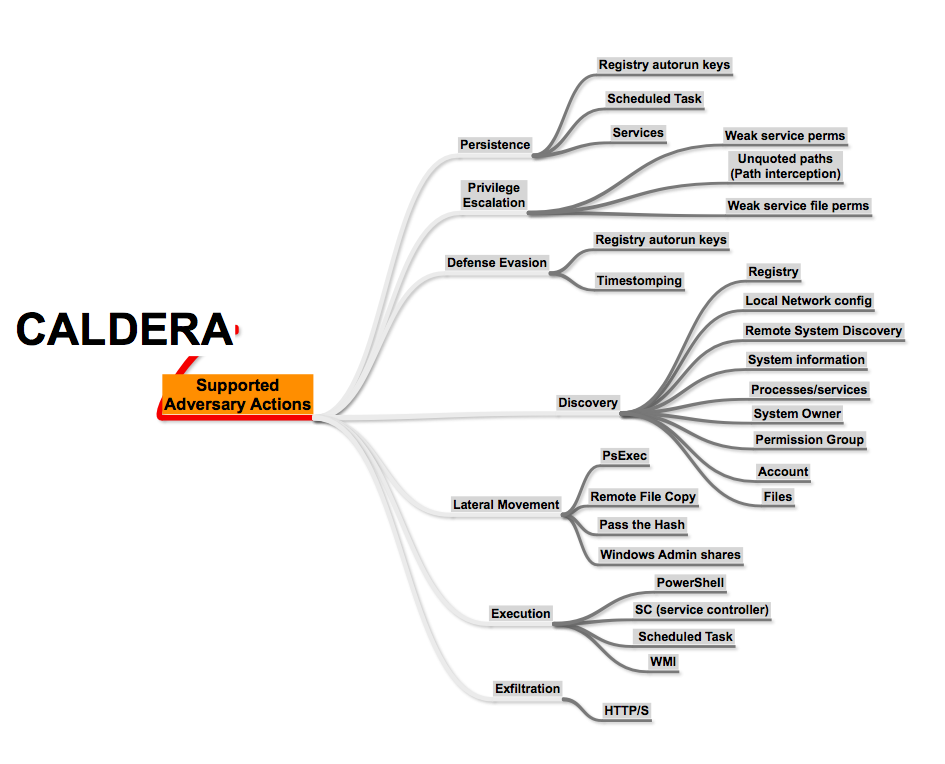
CALDERA is useful for defenders who want to generate real data that represents how an adversary would typically behave within their networks. Since CALDERA’s knowledge about a network is gathered during its operation and is used to drive its use of techniques to reach a goal, defenders can get a glimpse into how the intrinsic security dependencies of their network allow an adversary to be successful. CALDERA is useful for identifying new data sources, creating and refining behavioral-based intrusion detection analytics, testing defenses and security configurations, and generating experience for training.
Architecture
CALDERA consists of:
- Server
- Planner – Decision engine allowing CALDERA to chose actions
- Attacker Model – Actions available based on ATT&CK
- World Model – Representation of the environment
- Execution Engine – Drives actuation of techniques and updates the database
- Database – Stores knowledge learned about the environment
- HTTP Server
- Planner – Decision engine allowing CALDERA to chose actions
- Clients
- Agent – Client on endpoint systems used for communication
- RAT – Remote access tool used during operations to emulate adversary behavior
Comments are closed.