To remain ahead of defenders, APT organizations are continually upgrading their tactics and strategies. The following are the cases of prominent APT groups culled from materials made public by security businesses and institutions for July 2023.
APT28
APT28, commonly known as Fancy Bear, is one of the Advanced Persistent Threat (APT) organizations tracked by AhnLab. Threat Trend Report on APT organizations. APT28 is suspected of performing cyber intelligence or damaging operations with the assistance of certain countries. They are a nation-led threat group that is not driven by monetary gain. The report categorizes APT28 as a threat actor. They go by other names as well, such as Sofacy.
According to Google’s Threat Analysis Group, APT28, or Fancy Bear, is still active and focused on the conflict in Ukraine. They are a Russian government-backed threat outfit that has been conducting phishing attacks and distributing various malware against companies linked with the Pipeline Consortium (CPC). APT28 has been observed engaging in intelligence collection, information operations (IO), and leaking hacked data through platforms like Telegram.
APT29
APT29, also known as Cozy Bear or Nobelium, is a cyber intelligence or destructive advanced persistent threat (APT) outfit. This group is thought to be supported by various governments. APT29 is one of the nation-led threat groups highlighted in the Threat Trend Report on APT Groups for April 2023.
APT29 is recognized as a notable APT group in the May 2023 Threat Trend Report on APT Groups. According to the research, the information on APT groups in the report was taken from materials made public by security companies and institutions.
According to the information presented, APT29 is an active APT group engaged in cyber intelligence and damaging activities. To protect against APT29 and similar threat groups, organizations and people must be aware and employ effective cybersecurity measures.
APT31
APT31 is a cyber espionage entity with a China connection that seeks information to aid the Chinese government and state-owned corporations with political, economic, and military advantages. They have targeted a variety of industries, including government, international financial institutions, aerospace and defense firms, high-tech businesses, construction and engineering, telecommunications, media, and insurance.
Picus Security’s cyber threat intelligence assessment states that APT31 was active in East Asia in July 2023. They were part of the Mysterious Elephant threat group, which targeted Asia-Pacific countries. APT31 was also mentioned in the study as one of the top threat actors targeting the European region.
According to Kaspersky, the APT31 gang has launched a series of attacks targeting industrial groups. The goal of such attacks is to open a conduit for data leaks, and second-stage malicious software is employed to gather information from afflicted systems.
Camouflaged Hunter
A Camouflaged Hunter is a hunter who is proficient at blending in with their environment and evading discovery. This can be accomplished by wearing camouflage clothes, blending in with natural characteristics, and employing specialist strategies such as stalking and ambush.
Camouflaged hunters are frequently utilized in military and law enforcement operations because they may acquire intelligence, pursue suspects, and ambush opponents. Hunters and conservationists use them to watch wildlife without disturbing it.
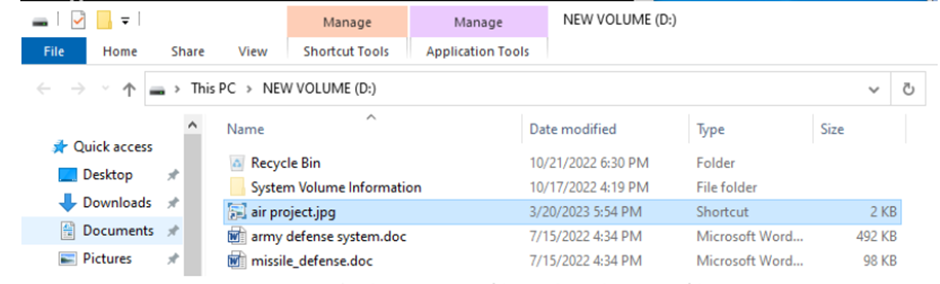
ThreatBook found the Camouflaged Hunter (APT-C-60) gang launching assaults with military-related topics like “missile defense.doc” and “army defense system.doc”. Malware is downloaded when a user clicks the LNK file within the virtual hard disk (VHD) file malware is downloaded and executed.
Charming Kitten
Charming Kitten is a state-sponsored advanced persistent threat (APT) group based in Iran. Other names for it include APT35, Phosphorus, Ajax Security Team, and NewsBeef.
Charming Kitten is well-known for using social engineering and spear phishing assaults on a diverse spectrum of victims, including government officials, military people, academics, journalists, and human rights activists. Attacks on essential infrastructure and businesses have also been linked to the group.
https://threatbook.io/blog/id/1090
Gamaredon
Gamaredon is a state-sponsored advanced persistent threat (APT) group based in Russia. Other names for it include Aqua Blizzard, Armageddon, Shuckworm, and UAC-0010.
Gamaredon is well-known for employing spear phishing operations against a diverse set of victims, including government officials, military people, corporations, and vital infrastructure groups. Attacks against foreign governments and international organizations have also been linked to the group.
Kimsuky
Kimsuky, also known as Velvet Chollima, is a cyber espionage outfit based in North Korea that has been operating since at least 2012. They primarily target South Korean government, military, academic, and think tank institutions. Kimsuky employs spear-phishing techniques and custom-built malware to steal sensitive information and gather intelligence.
https://asec.ahnlab.com/en/55944/
https://asec.ahnlab.com/en/55944/
Konni
Konni is a cyber espionage group that mostly targets South Korean organizations. They’ve been there since at least 2014, and they’re notorious for using spear-phishing tactics to transmit malware, primarily through Microsoft Excel documents. Konni has also been seen carrying out waterhole attacks and employing steganography techniques to conceal harmful code.
Lazarus
Lazarus, also known as Hidden Cobra, is a state-sponsored North Korean terror group. They are well-known for their involvement in high-profile cyber assaults, such as the Sony Pictures Entertainment breach in 2014 and the WannaCry ransomware outbreak in 2017. Lazarus is a participant in cyber espionage, data theft, and financially driven attacks.
One of the most famous Lazarus-related assaults was the 2014 Sony Pictures Entertainment breach. The organization targeted Sony Pictures’ network, leaking critical information, disrupting operations, and causing the firm severe financial and reputational harm. Lazarus was also behind the devastating WannaCry ransomware assault in 2017, which infected hundreds of thousands of systems around the world and caused severe disruptions in a variety of industries.
https://blogs.jpcert.or.jp/en/2023/07/dangerouspassword_dev.html
https://asec.ahnlab.com/en/55369/
Mustang Panda
Mustang Panda, also known as RedDelta or BRONZE PRESIDENT, is a Chinese-speaking APT organization predominantly targeting Southeast Asian institutions, particularly Myanmar. They are primarily concerned with gathering geopolitical information about Myanmar’s government, military, and ethnic minority groups. Mustang Panda is well-known for delivering targeted malware via smart site hacks and spear-phishing tactics.
Patchwork
Patchwork, also known as Dropping Elephant or Chinastrats, is an APT organization that primarily targets entities in Southeast Asia, specifically India, Pakistan, and Southeast Asian countries. They have been active since at least 2014 and use a range of approaches to deliver malware and obtain access to targeted networks, including spear-phishing emails and watering hole assaults.
Red Eyes
Red Eyes is a persistent threat (APT) group that has been active since at least 2010. While there is less public material accessible on Red Eyes than on other APT organizations, certain details regarding their actions and targets have emerged.
Governments and diplomatic missions, notably in Eastern Europe and Central Asia, are the primary targets of Red Eyes. Their actions have primarily targeted Ukraine, Poland, and Lithuania. The gang is notorious for engaging in cyber espionage and data theft in order to obtain sensitive information and intelligence for political or economic goals.
Space Pirates
PTSecurity has disclosed new information about the Space Pirates group, which has been targeting Russia’s aerospace and energy businesses, as well as those of Georgia and Mongolia.
The Space Pirates organization has purportedly been active since 2017 and speaks Chinese. The Space Pirates group focuses its attacks on specific targets and conducts extensive research to understand the network infrastructure and security mechanisms utilized by enterprises.
The Space Pirates are linked to other Chinese groups such as APT27, APT41, TA428, and Mustang Panda.
Turla
Turla is a state-sponsored Advanced Persistent Threat (APT) group that has been active since at least 2007. Other names for it include Snake, Uroburos, and Waterbug. Turla is thought to be of Russian descent and has been linked to Russian spy agencies.
Unclassified
Storm-0558 (a temporary group name assigned by Microsoft) acquired illegal access to Exchange Online (OWA) and Outlook.com, according to Microsoft.26 A third party is reported to have accessed the email data of roughly 25 organizations, including US government entities, as well as personal accounts linked to these organizations. Storm-0978 also leveraged Microsoft Office and the Windows HTML remote code execution zero-day vulnerability (CVE-2023-36884) against national defense and government agencies in Europe and North America in another attack. Trend Micro discovered a ShadowPad variant that infected targets via a modified installation file of the Pakistani government’s E-Office program, however because ShadowPad is used by various Chinese-speaking groups, it could not be connected to a specific APT group.
