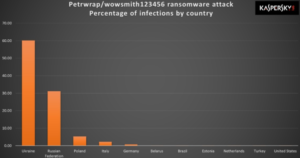
On 27 June 2017, a major global cyberattack began (Ukrainian companies were among the first to state they were being attacked), utilizing a new variant of Petya. On that day, Kaspersky Lab reported infections in France, Germany, Italy, Poland, the United Kingdom, and the United States, but that the majority of infections targeted Russia and Ukraine, where more than 80 companies initially were attacked, including the National Bank of Ukraine. ESETestimated on 28 June 2017 that 80% of all infections were in Ukraine, with Germany second hardest hit with about 9%. Russian president Vladimir Putin’s press secretary, Dmitry Peskov, stated that the attack had caused no serious damage in Russia. Experts believed this was a politically-motivated attack against Ukraine, since it occurred on the eve of the Ukrainian holiday Constitution Day.
Kaspersky dubbed this variant “NotPetya”, as it has major differences in its operations in comparison to earlier variants. McAfee engineer Christiaan Beek stated that this variant was designed to spread quickly, and that it had been targeting “complete energy companies, the power grid, bus stations, gas stations, the airport, and banks”.


It was believed that the software update mechanism of M.E.Doc — a Ukrainian tax preparation program that, according to F-Secure analyst Mikko Hyppönen, “appears to be de facto” among companies doing business in the country—had been compromised to spread the malware. Analysis by ESET found that a backdoor had been present in the update system for at least six weeks prior to the attack, describing it as a “thoroughly well-planned and well-executed operation”. The developers of M.E.Doc denied that they were entirely responsible for the cyberattack, stating that they too were victims.
On July 4, 2017, Ukraine’s cybercrime unit seized the company’s servers after detecting “new activity” that it believed would result in “uncontrolled proliferation” of malware. Ukraine police advised M.E.Doc users to stop using the software, as it presumed that the backdoor was still present. Analysis of the seized servers showed that software updates had not been applied since 2013, there was evidence of Russian presence, and an employee’s account on the servers had been compromised; the head of the units warned that M.E.Doc could be found criminally responsible for enabling the attack because of its negligence in maintaining the security of their servers.
Attack Scenario
FireEye detected malicious Microsoft Office RTF documents that leverage CVE-2017-0199, a previously undisclosed vulnerability. This vulnerability allows a malicious actor to download and execute a Visual Basic script containing PowerShell commands when a user opens a document containing an embedded exploit. FireEye has observed Office documents exploiting CVE-2017-0199 that download and execute malware payloads from different well-known malware families.
FireEye shared the details of the vulnerability with Microsoft and has been coordinating public disclosure timed with the release of a patch by Microsoft to address the vulnerability, which can be found here.
The vulnerability bypassed most mitigations prior to patch availability; however, FireEye email and network products detected the malicious documents. FireEye recommends that Microsoft Office users apply the patch from Microsoft.
The attack occurs in the following manner:
- A threat actor emails a Microsoft Word document to a targeted user with an embedded OLE2 embedded link object
- When the user opens the document, winword.exe issues a HTTP request to a remote server to retrieve a malicious HTA file
- The file returned by the server is a fake RTF file with an embedded malicious script
- Winword.exe looks up the file handler for application/hta through a COM object, which causes the Microsoft HTA application (mshta.exe) to load and execute the malicious script
Ransomware includes:
- Modified EternalBlue exploit
- A vulnerability in a third-party Ukrainian software product
- A second SMB network exploit
Possible IP addresses:
185.165.29.78
84.200.16.242
111.90.139.247
95.141.115.108
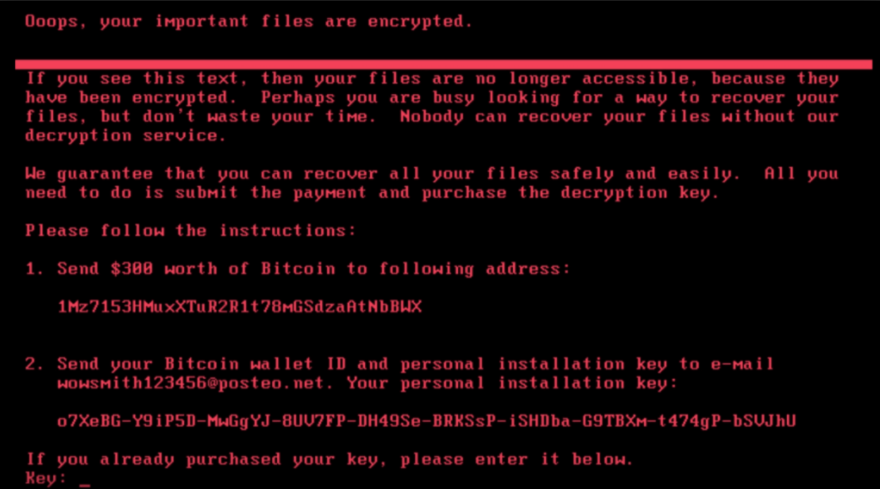
Email:
wowsmith123456@posteo.net
iva76y3pr@outlook.com // by WhiteWolfCyber
carmellar4hegp@outlook.com // by WhiteWolfCyber
amanda44i8sq@outlook.com // by WhiteWolfCyber
gabrielai59bjg@outlook.com
christagcimrl@outlook.com
amparoy982wa@outlook.com
rachael052bx@outlook.com
sybilm0gdwc@outlook.com
christian.malcharzik@gmail.com
Email forms and attachment:
The subject in this case are formed like that (for targed "targed.emailName@targedDomain.com"):
targed.emailName
The body:
Hello targed.emailName,
You will be billed $ 2,273.42 on your Visa card momentarily.
Go through attachment to avoid it.
Password is 6089
With appreciation!
Prince
Attached file name:
Scan_targed.emailName.docPossible Prevention along with Blocking IOCs
Looks like if you block C:\Windows\perfc.dat from writing/executing - stops #Petya. Is used for rundll32 import.
https://twitter.com/HackingDave/status/879779361364357121
Analysis:
- https://virustotal.com/fr/file/027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745/analysis/
- https://www.hybrid-analysis.com/sample/027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745?environmentId=100
- https://www.hybrid-analysis.com/sample/fe2e5d0543b4c8769e401ec216d78a5a3547dfd426fd47e097df04a5f7d6d206?environmentId=100
- https://www.hybrid-analysis.com/sample/ee29b9c01318a1e23836b949942db14d4811246fdae2f41df9f0dcd922c63bc6?environmentId=100
- https://twitter.com/PolarToffee/status/879709615675641856